 Data Masking/Protection
Data Masking/Protection
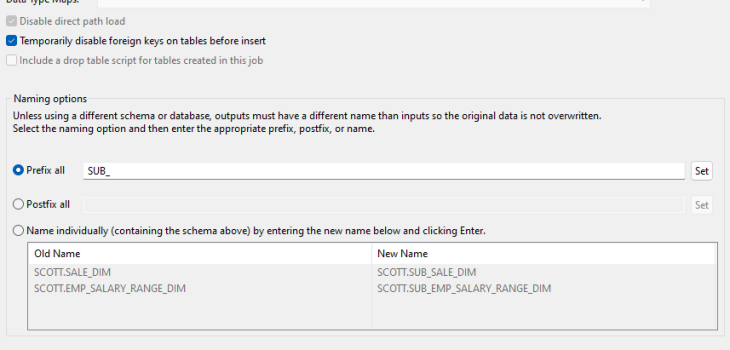
What Is Database Subsetting? How to Subset a Database.
Once a database exceeds a certain size, it becomes expensive — and risky from a security perspective — to provide full-size copies for development, testing, and training. Read More