Connecting MS SQL to IRI Workbench
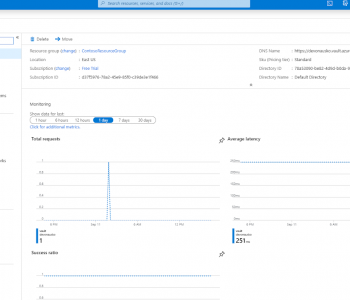
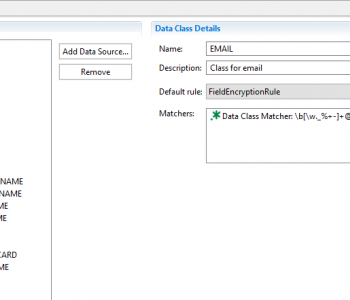
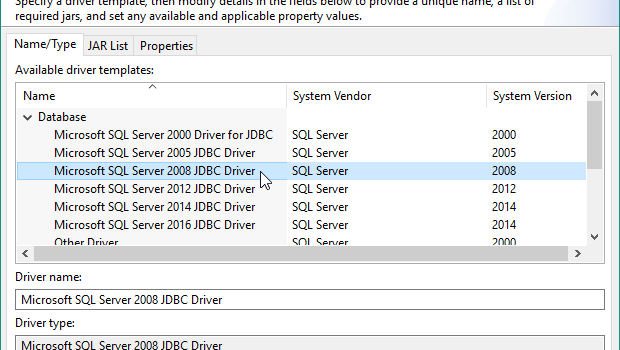
Whether your SQL Server database is on-premise or in a cloud enviroment like Azure, its data is accessible for movement and manipulation in IRI Workbench-supported products like CoSort, FieldShield, DarkShield, NextForm and RowGen, or the IRI Voracity platform which includes them all. Read More