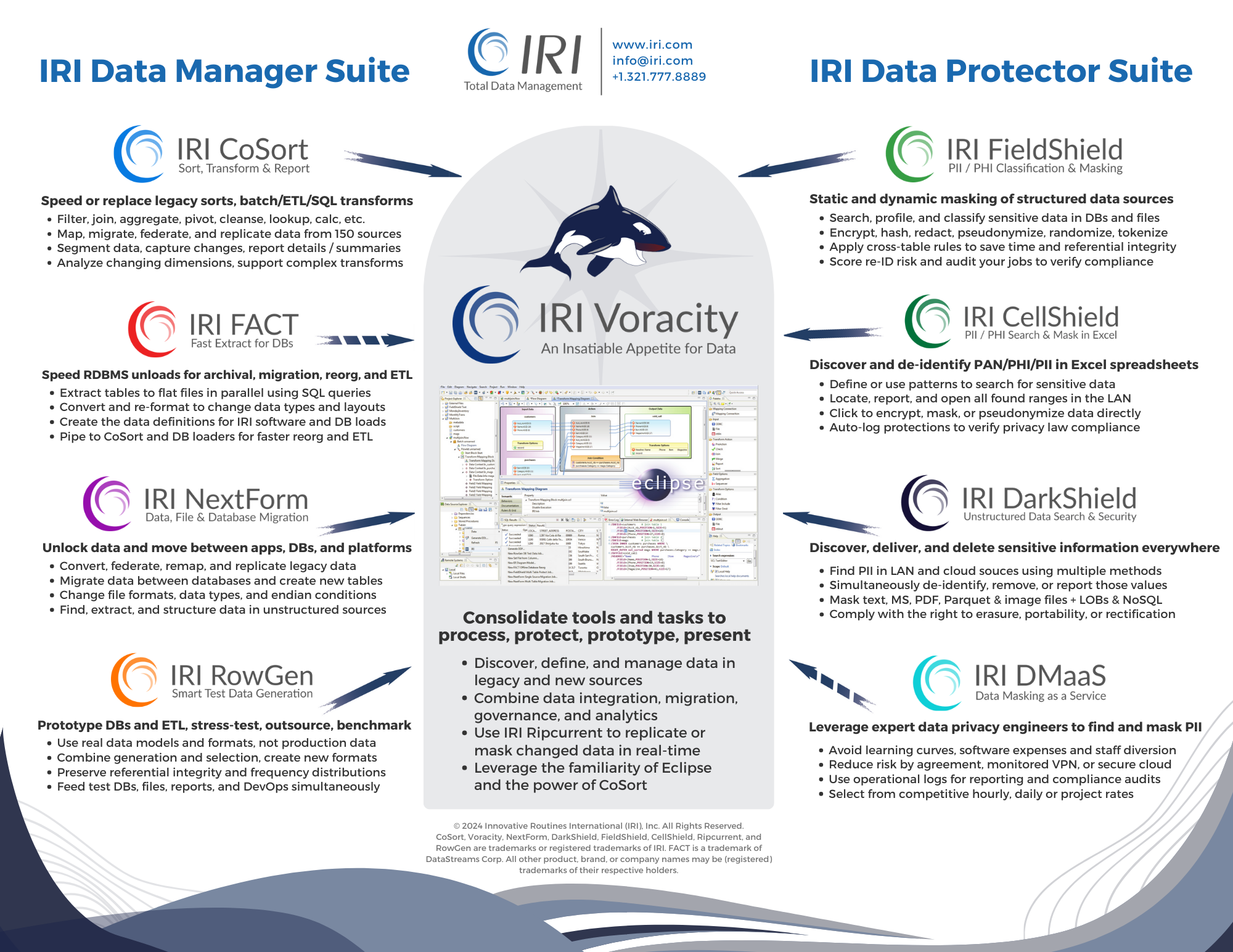
Award-Winning Data Masking Tools
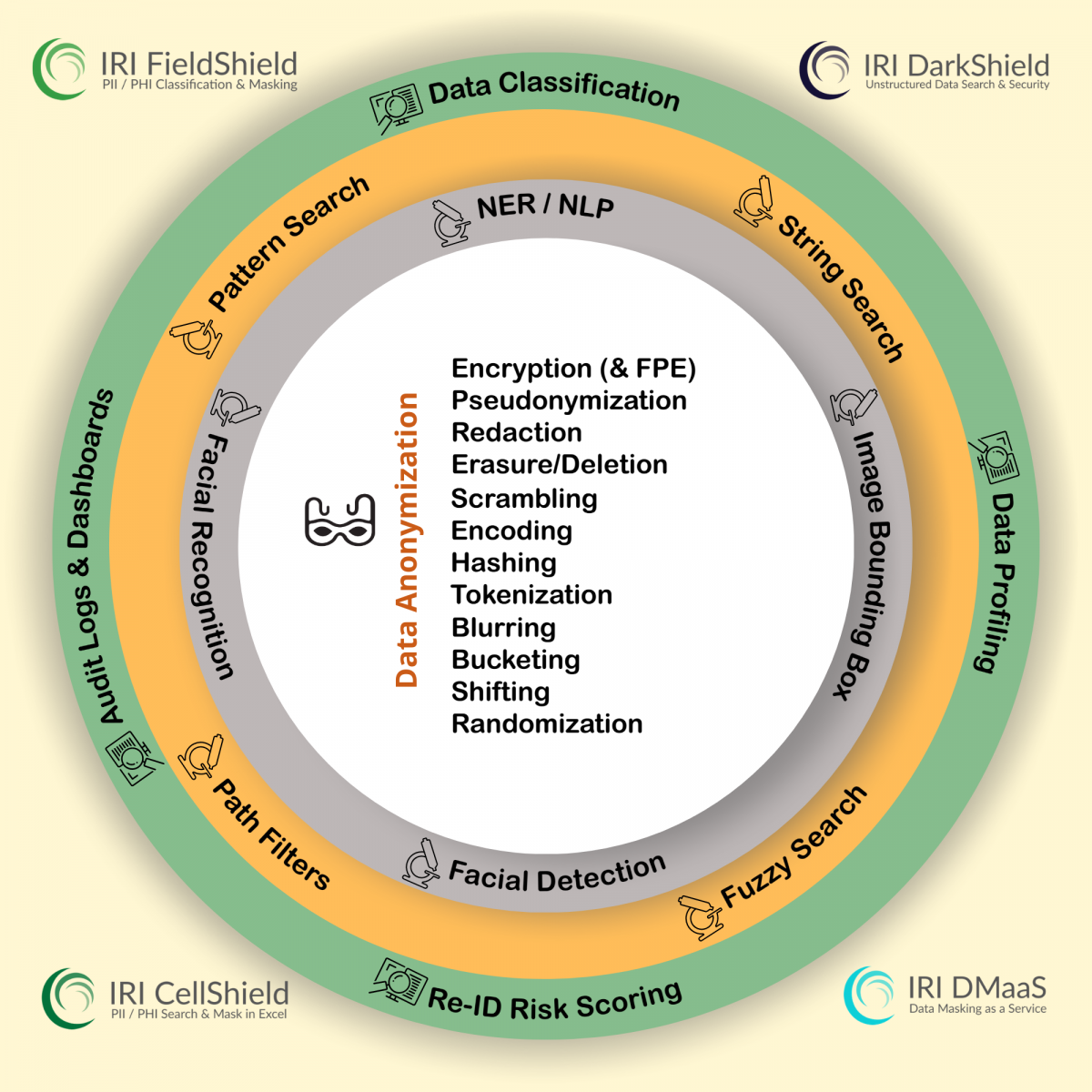
Renowned self-hosted data classification, PII discovery, and data masking tools in the IRI Data Protector suite and IRI Voracity data management platform will: catalog, find, and mask personally identifiable information (PII) and other "data at risk" in multiple sources. Each one will help you comply (and prove compliance) with the CPRA, CIPSEA, FERPA, HIPAA/HITECH, PCI DSS, and SOC2 in the US, and international data privacy laws like the GDPR, DPDPA, KVKK, LGPD, LOPD, PDPA, PIPEDA and POPIA.
Co-located and compatible IRI tooling in Voracity, including IRI RowGen, can also synthesize realistic test data from scratch, and produce referentiallycorrect (and optionally masked) database subsets.
IRI and its authorized partners around the world can help you implement fit-for-purpose data anonymization, test data management, AI model compliance, and data breach mitigation solutions using these technologies if you need help. For more information, link to the products and use cases below. Schedule a free online demonstration or an on-site evaluation here.

Structured Data Masking
FieldShieldclassifies, discovers, de-identifies, risk-scores, anonymizes and audits PII in relational databases, sequential files, ASN.1 CDRs, ACH and Fedwire files, and Excel (XLS/X) spreadsheets.
Learn MoreStructured, Semi- & Unstructured Data Masking
DarkShield classifies, discovers, and masks PII in RDBsand flat files, too, plus: free text, JSON and XML, HL7/X12/FHIR EDI, Parquet, audio, .SQL, and log files; MS Office (Word, Excel and Powerpoint) and PDF documents, NoSQL databases and Splunkindexes; plus, DICOM medical studies, common image formats, and signatures. Handwriting and faces are in progress.
Learn MoreExcel® Data Masking
CellShieldworks directly in Excel to find, report on, mask, and audit changes to PII in Excel columns and values -- on multiple sheets LAN-wide or in Office 365.
Learn MoreData Masking as a Service
This is not a cloud-based SaaS solution - in fact IRI software runs on-premise. DMaaSin thisecase means engineers in the US and abroad help do the work of classifying, finding, masking, and risk-scoring PII for you on your systems only.
Learn MoreLearn More
Compare the capabilities of IRI's award-winning data masking tools with this matrix, and peruse IRI's proven test data solutions here. Dive deeper with the slide deck and our article on "startpointsecurity" below.
Test Data Synthesis

Use the proven IRI data masking tools above, the IRI RowGen test data synthesis package, or the IRI Voracity data management platform which includes them all, to: subset, create, or virtualize safe, intelligent test data in DB, file, API, and report targets for ETLprototypes, DevOps, benchmarking, etc.
Learn MoreUse Cases
The IRI Data Protector suite's constituent products address:
- Data Discovery and Classification for data security, quality/MDM, etc.
- Data Governance, Risk Management, and Compliance (GRC) initiatives
- Data Loss Prevention (DLP) and De-ID for HIPAA-and GDPR-covered entities
- Re-ID risk scoring and PHI blurring for Expert Determination Method compliance
- Static Data Masking (SDM) and Dynamic Data Masking (DDM) applications
- Encryption, hashing, and tokenization of PANsfor PCI DSS
- Prototyping DB/ETL operations, DevOps and high volume data stress-testing
These data masking tools and data-centric security solutions are also critical complements to device and perimeter (network) security solutions which cannot address insider attacks.
Licensing costs for the masking tools typically depend how many hostname executables, you need. See this FAQ on pricing.