 Big Data
Big Data
Connecting Databricks Delta Tables
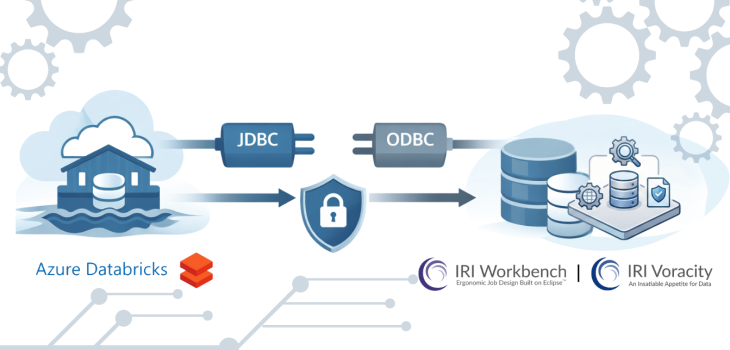
Abstract: This article covers the necessary JDBC and ODBC connectivity steps to reach Azure Databricks Delta tables from IRI Workbench and the CoSort SortCL engine used in structured data management operations in the Voracity platform ecosystem, especially IRI FieldShield data classification and masking jobs. Read More