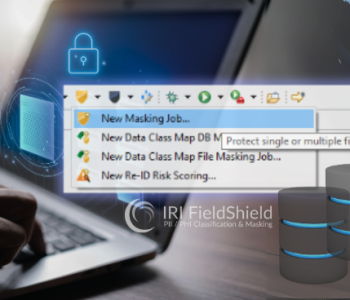
How to Mask PII in a Database
First released in 2011, the IRI FieldShield database data masking tool helps you classify, find, and de-identify personally identifiable information (PII) or other sensitive data in structured relational database (RDB) sources. Read More