Data Masking/Protection
Data Masking/Protection
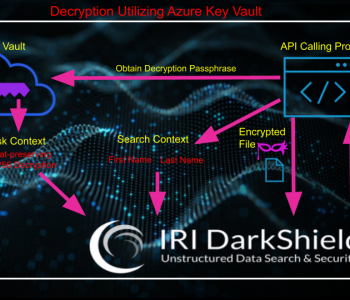
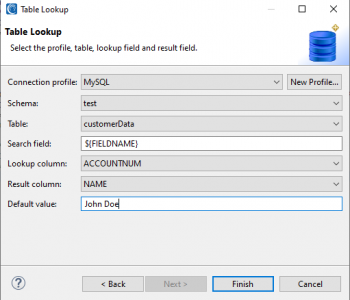
Keeping AI Models GDPR-Compliant with Data Masking
Maintaining GDPR compliance while creating AI models doesn’t have to feel impossible. The key lies in using GDPR data masking techniques, which safeguard privacy without hurting how well models work. Read More