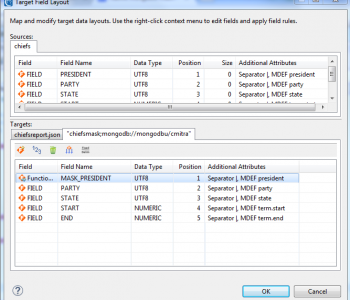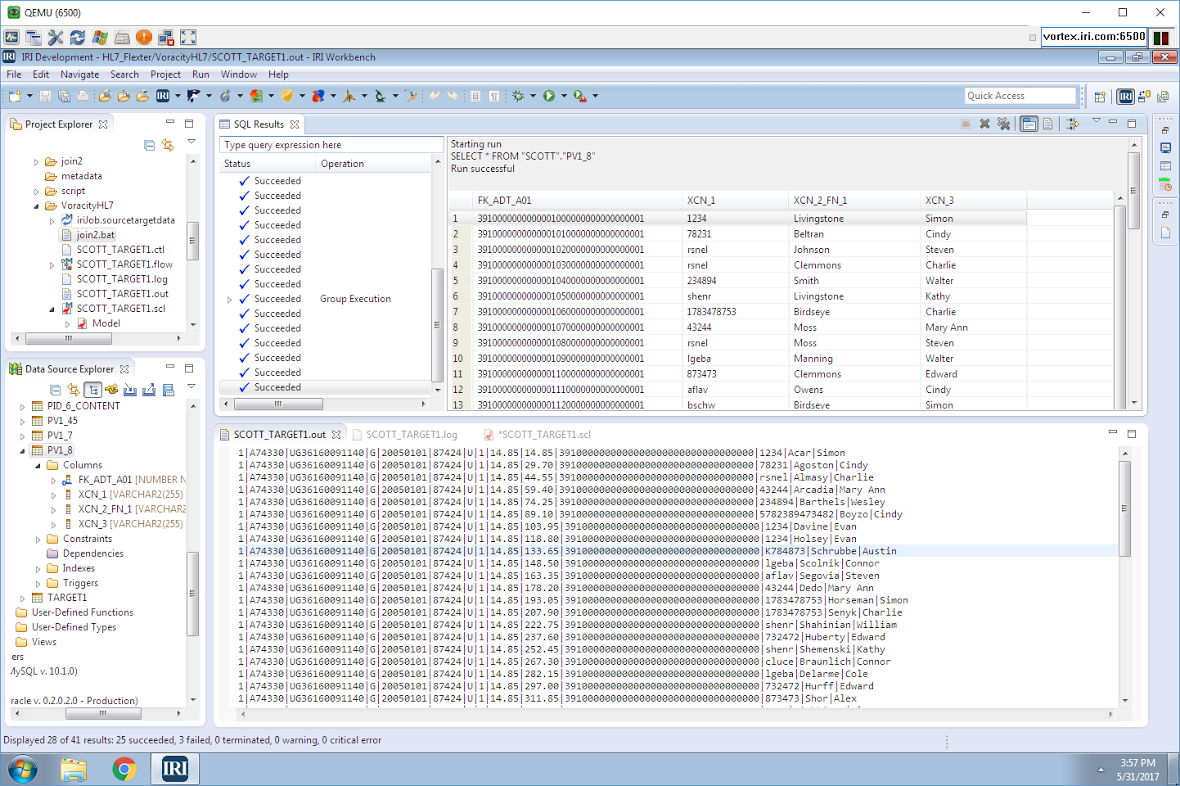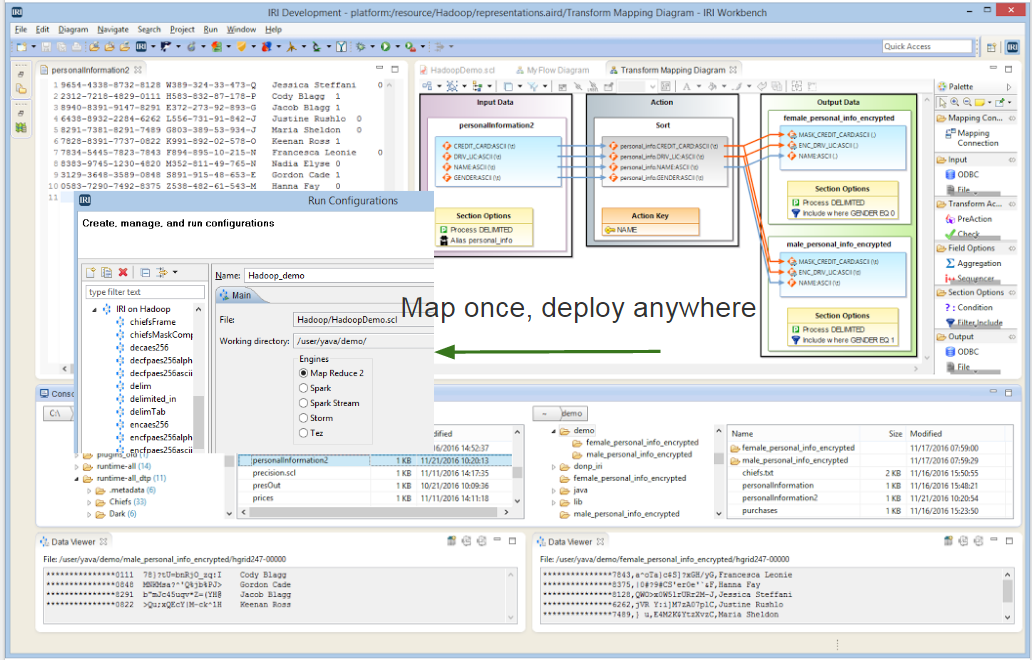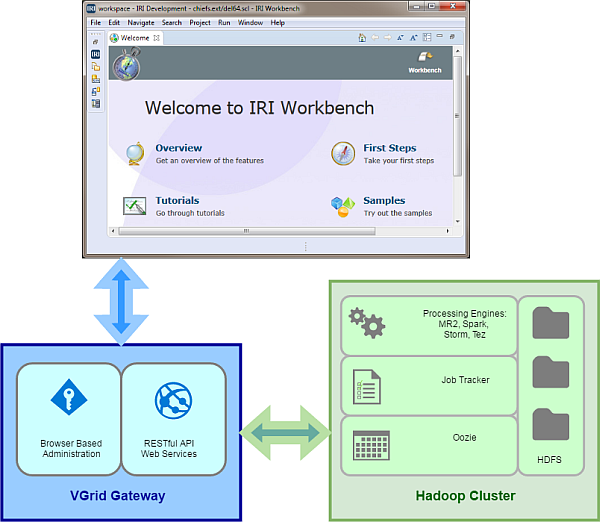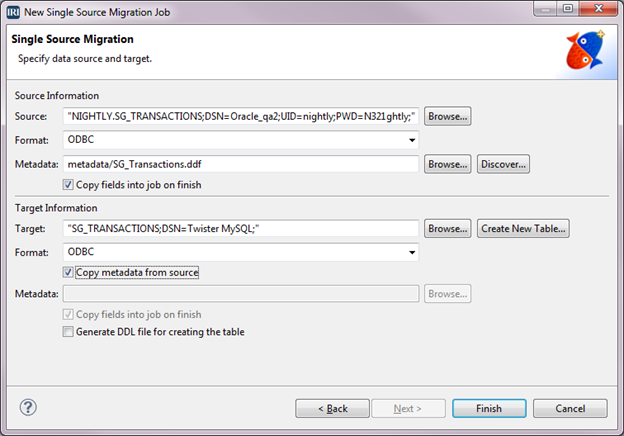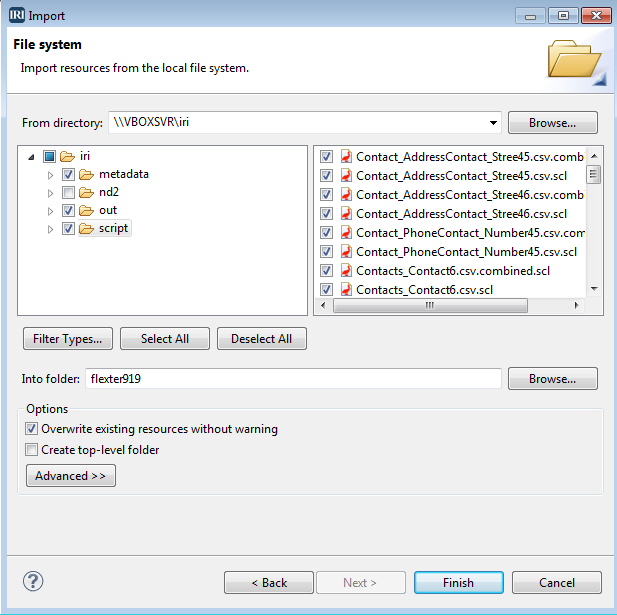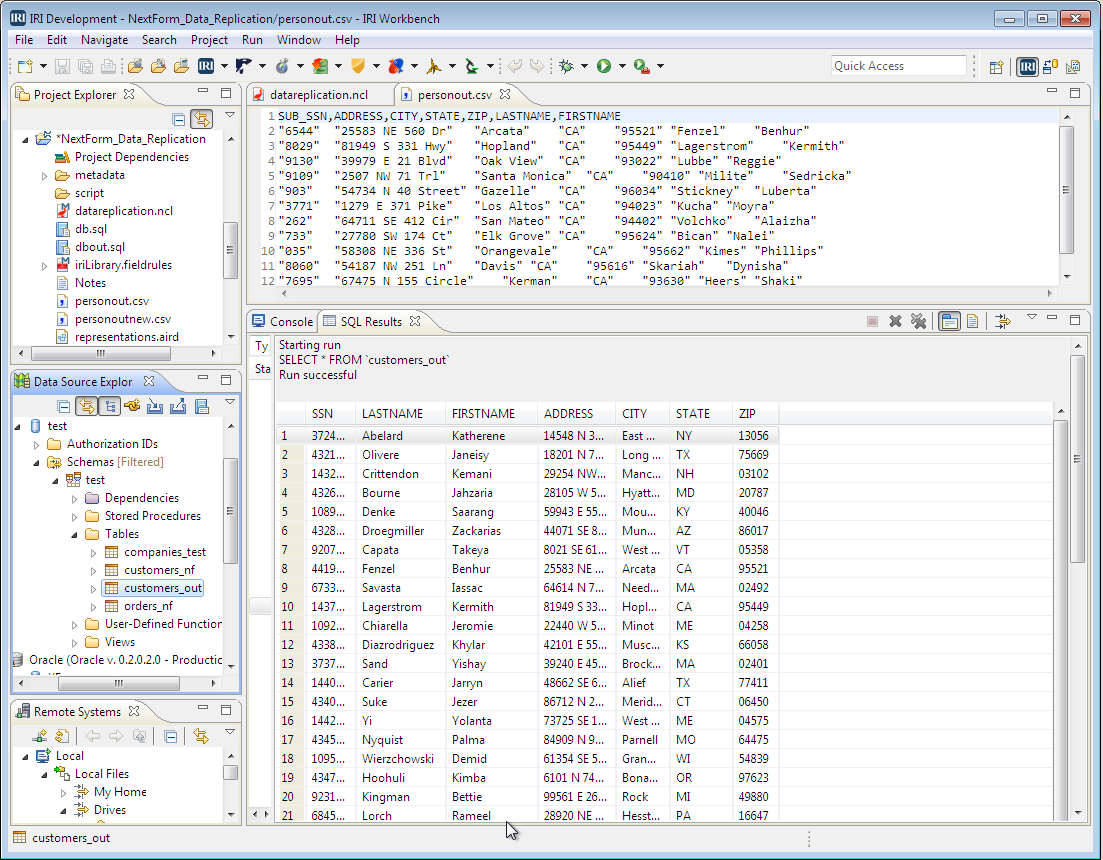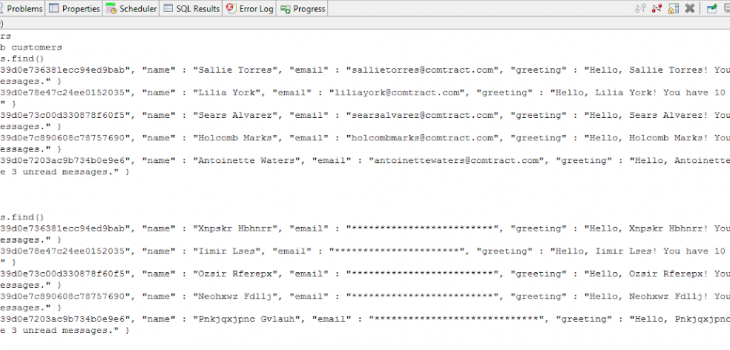
Masking PII in MongoDB, Cassandra, and Elasticsearch with DarkShield:…
Editor’s Note:
As of 2024 and DarkShield V5, the search and masking methods for these NoSQL DBs has been upgraded; please refer to the discussion and demonstration in this updated article instead! Read More