 Business Intelligence (BI)
Business Intelligence (BI)
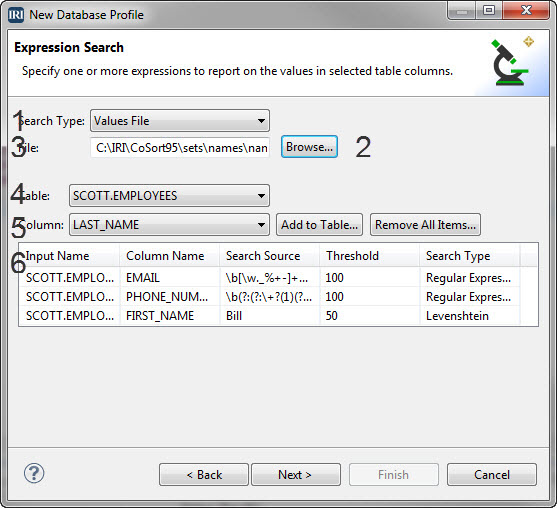
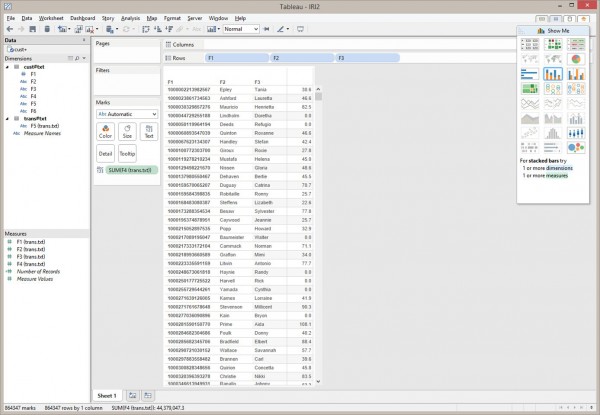
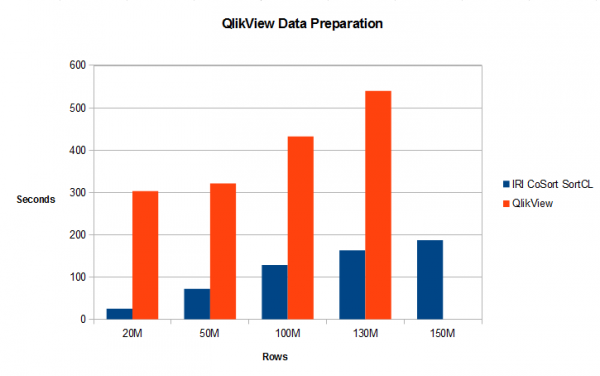
How to QlikView 12X Faster with CoSort
Introduction: As with multiple BI platforms discussed throughout this section of the IRI blog site, this article analyzes the relative data preparation performance (and benefit) of using its external data wrangling engine – via the IRI CoSort product or Voracity platform — with QlikView when ‘big data’ sources are involved. Read More