
Masking PII in SQL Files
One of the most common targets for PII theft is data within databases. This blog is replete with examples of how to find and mask that PII residing in the schema of production or test databases using IRI FieldShield or DarkShield.
A more obscure, but still potentially vulnerable source of database PII resides .sql dump files. SQL dump files are the result of exporting the contents and metadata of a database that are then saved as SQL statements in a text file.
The primary purpose of SQL dumps is backup and recovery, migrating between systems, and data provisioning for testing. When data from a production database is exported and dumped into a .sql file, a new vector for accessing the PII contained in that database is created.
Several high-profile incidents highlight how dangerous unsecured SQL files can be:

-
Navy Federal Credit Union (May 2024): 378 GB of unencrypted SQL backups were left publicly accessible in an Amazon S3 bucket.
-
BigBasket (2020): The Indian online grocer experienced a large data leak, believed to include compromised SQL exports (or SQL injection).
-
A tech news site, BGR India (2020): Unsecured AWS S3 buckets exposed SQL backups of its WordPress site database.
-
A mining company in Indonesia, Karunia Group (August 2025): SQL dumps from the company’s internal HR system were leaked.
DarkShield .SQL File Support
In the latest release of IRI DarkShield, .sql files are now supported for data discovery and masking. The ability to handle .sql files in DarkShield gives users the ability to mask sensitive data in backup files when it is not possible to allow DarkShield access to the database directly.
Handling .sql files is done no differently than any other type of file in a DarkShield Job. Just be sure to indicate this file type among any others that DarkShield will search and mask from the defined on-premise and/or cloud folders it reads.
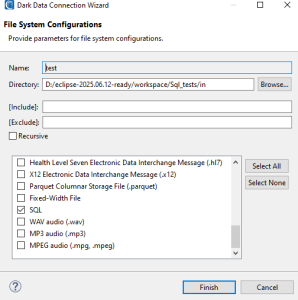
To learn how to create a DarkShield File job from the Workbench GUI, read this article or watch this video.
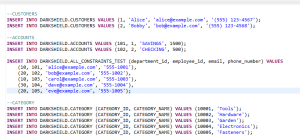
Before DarkShield
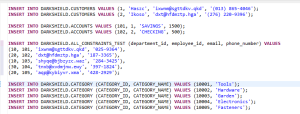
After DarkShield
This example shows the application of format-preserving encryption (one of many available, data-class-specific IRI masking functions) on the name, email and phone number values in the insert statements:
For help with data classification (discovery) and masking of PII or other sensitive data in SQL files (or other sources – structured, semi-structured, or unstructured), please email darkshield@iri.com.










