Navigating DPDPA Compliance
Introduction
The enactment of the Digital Personal Data Protection Act (DPDPA) 2023 on August 11, 2023, marks a significant evolution in India’s data protection landscape. This new legislation introduces stringent requirements for the management and protection of personal data and tries to balance individual rights and organizational responsibilities.
Key DPDPA Definitions
A Data Fiduciary is anyone who alone or in conjunction with others determines the purpose and means of processing of personal data. A Data Principal is the individual to whom the personal data relates, with a special focus on children or the disabled and their lawful guardians, but of course, this pretty much means everyone in a family.
A Data Processor is a person who processes personal data on behalf of a Data Fiduciary. Processing means fully or partly automated operations on digital personal data, including its collection, storage, use, disclosure, or restriction/erasure. And, a Data Protection Officer is the person appointed by the “significant” Data Fiduciary.
The Importance of Compliance
Non-compliance with the DPDPA can lead to substantial penalties, including fines up to 250 crore INR (roughly US $30M). Such measures highlight the critical need for data-centric protection practices that can maintain compliance and uphold public trust.
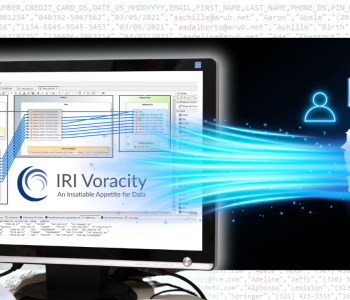
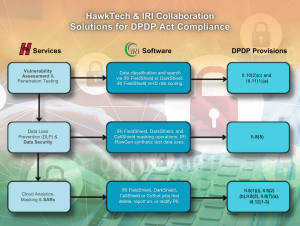
IRI has recently partnered with Indian data consultancy HawkTech Advance Solutions in Noida to apply expert vulnerability assessment services with IRI Data Protector Suite software like IRI FieldShield or DarkShield to classify, discover, and mask PII before a data breach happens. This same combination of expertise and technology also aims to satisfy DPDPA Subject Access Requests (SARs).

Data Discovery and Masking for Compliance
In general, if breached data was rendered unidentifiable by prior redaction, erasure, or pseudonymisation for example, it cannot be reused. Such prevention of data misuse should thus preclude any DPDPA penalties.
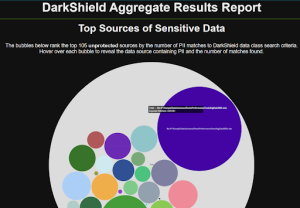
If it is too late, however, and a breach of unmasked data has occurred, the DPDPA requires notification of the affected Data Principals about what has been exposed. Data Fiduciaries must identify (by searching for all names or Aadhaar numbers for example) and notify those whose unmasked values were found (and thus exposed). They can do this through the IRI product search logs; see this page and details in the next section.
Key DPDPA Provisions and IRI Technology Applications
Following are the general requirements of the DPDPA and specific IRI solutions to them. Let’s start with those pertaining to the Data Fidicuciary’s responsibility to obtain consent to process a Data Principal’s data, and to maintain an audit trail around it:
Chapter II, Obligations of Data Fiduciary,
5. (1) Every request made to a Data Principal under section 6 for consent shall be accompanied or preceded by a notice given by the Data Fiduciary to the Data Principal, informing her,—
(i) the personal data and the purpose for which the same is proposed to be processed;
Chapter II, Section 10:
(2) The Significant Data Fiduciary shall—
(c) undertake the following other measures, namely:—
(i) periodic Data Protection Impact Assessment, which shall be a process comprising a description of the rights of Data Principals and the purpose of processing of their personal data, assessment and management of the risk to the rights of the Data Principals, and such other matters regarding such process as may be prescribed;
(ii) periodic audit
and
Chapter III, Section 11:
(1) The Data Principal shall have the right to obtain from the Data Fiduciary to whom she has previously given consent, including consent as referred to in clause (a) of section 7 (hereinafter referred to as the said Data Fiduciary), for processing of personal data, upon making to it a request in such manner as may be prescribed,—
(a) a summary of personal data which is being processed by such Data Fiduciary
and the processing activities undertaken by that Data Fiduciary with respect to such personal data;
These clauses effectively require the Data Fiduciary to locate, extract, and provide the Data Principal with his/her record(s) for review. IRI software users can pull those records from tables or files in a simple (e.g., FieldShield) job script using the SQL SELECT (query) syntax, or an /INCLUDE filter on the Data Principal’s name or other value in a unique identifier column.
Similarly, an IRI DarkShield search through structured, semi-structured, or unstructured sources can optionally save the person’s name or other unique attribute/s (e.g., a phone number or email address) in human or machine-readable search logs.
Chapter II, 5. (2)(b), the Data Fiduciary may continue to process the personal data until and unless the Data Principal withdraws her consent.
Once a Data Principal has withdrawn their consent, the Data Fiduciary must be able to find and delete (or otherwise “cease processing”) all data associated with that Data Principal. See the section on erasure below.
Note that an /OMIT WHERE clause in FieldShield jobs may be added to allow for the exigencies to this however, as foreseen in:
Chapter II, Section 7 (II):
(c) for the performance by the State or any of its instrumentalities of any function under any law for the time being in force in India or in the interest of sovereignty and integrity of India or security of the State;
(d) for fulfilling any obligation under any law for the time being in force in India on any person to disclose any information to the State or any of its instrumentalities, subject to such processing being under the provisions regarding disclosure of such information in any other law for the time being in force;
(e) for compliance with any judgment decree or order issued under any law for the time being in force in India, or any judgment or order relating to claims of a contractual or civil nature under any law for the time being in force outside India;
(f) for responding to a medical emergency involving a threat to the life or immediate threat to the health of the Data Principal or any other individual;
(g) for taking measures to provide medical treatment or health services to any individual during an epidemic, outbreak of disease, or any other threat to public health;
(h) for taking measures to ensure safety of, or provide assistance or services to, any individual during any disaster, or any breakdown of public order.
Robust Data Discovery Is Needed for Audit, Consent, Data Protection and More
The sections above mean that the Data Fiduciary needs – for risk assessment, management, and summarization purposes – to know where the Data Principal‘s PII is stored. Again, this is something that IRI DarkShield can discover in structured, semi-structured, and unstructured sources on-premise or in the cloud from searches that produce logs described in features #1, 3, and 7 listed here.
The need for discovery of both direct and indirect Data Principal identifies is also a condition precedent to meeting DPDPA security and SAR requirements, starting with data protection through PII data masking functions, per:,
Chapter II, Section 8:
(5) A Data Fiduciary shall protect personal data in its possession or under its control, including in respect of any processing undertaken by it or on its behalf by a Data Processor, by taking reasonable security safeguards to prevent a personal data breach.
The consistent application of obfuscation functions like redaction, removal, pseudonymization, scrambling, encryption, and blurring – all of which are provided and configurable in IRI FieldShield and DarkShield – provides those safeguards and production environments, as well as realism and referential integrity in test environments.
In addition to data protection, Data Principals have the right to rectification so that the data being processed or stored by the Data Fiduciary is up to date and/or corrected:
Chapter III, Section 12:
12. (1) A Data Principal shall have the right to correction, completion, updating and erasure of her personal data for the processing of which she has previously given consent, including consent as referred to in clause (a) of section 7, in accordance with any requirement or procedure under any law for the time being in force.
(2) A Data Fiduciary shall, upon receiving a request for correction, completion, or updating from a Data Principal,
(a) correct the inaccurate or misleading personal data;
(b) complete the incomplete personal data; and
(c) update the personal data.
This right to rectification means the Data Fiduciary must find and fix the Data Principal’s data, which could exist in different silos. In structured sources, changing values can be done with a lookup transformation or conditional field statement in a FieldShield job.
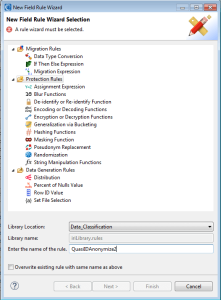
If the data is in structured, semi-structured and/or unstructured sources, it’s possible to set up a DarkShield pseudonymization rule to auto-substitute a particular person’s PII in multiple data sources. This can be done via specifically named data classes that refer to a new value placed in the relevant replacement set file.
Finally, Data Principal have the right to erasure, per the GDPR right to be forgotten:
Chapter III, Section 12,
- (3) A Data Principal shall make a request in such manner as may be prescribed to the Data Fiduciary for erasure of her personal data, and upon receipt of such a request, the Data Fiduciary shall erase her personal data unless retention of the same is necessary for the specified purpose or for compliance with any law for the time being in force.
The “Right to be Forgotten” article (re: GDPR) explains how to do this in each IRI data masking product.
Implementation Scenarios and Best Practices
Implementing these solutions requires strategic planning and proactive management of data protection measures:
- Vulnerability Assessments: Engage with the experts at HawkTech to analyze and test your systems for their risk from cyber attacks.
- Proactive Data Protection: Deploy IRI FieldShield or DarkShield to perform continuous data scans, and masking sensitive data so it’s secure and compliant well before any potential breach occurs.
- Responsive Data Management Post-Breach: If your data was not pre-masked, you can still use the built-in data classification and discovery features in these tools to identify, report on the exposed data to meet notification requirements. And of course, you can use the masking functions to neutralize future breaches in relevant data silos and sources.
Conclusion and Call to Action
The Digital Personal Data Protection Act 2023 sets forth rigorous standards that redefine data privacy and security. By leveraging HawkTech’s expert services in India with best-in-class IRI data classification, discovery, and masking software, you can comply with the law’s many requirements, and strengthen the security posture of your data processing and development infrastructure.
Click here to contact HawkTech in India, and here to contact IRI. Please tell us about your environment, timeline, and availability for an online meeting and demonstration.