Data Masking/Protection
Data Masking/Protection
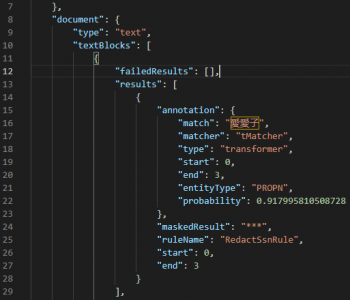
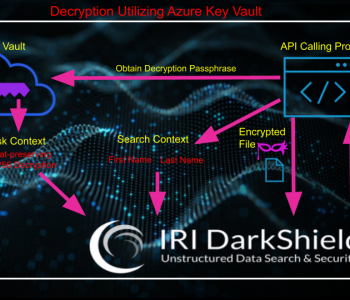
Masking RDB Data in the DarkShield GUI
Editor’s Note: This article is part of a series of articles on using DarkShield to search and mask sensitive data in relational databases. This new support for RDB sources in DarkShield can augment or replace IRI FieldShield support for the same data classes, locational searches and masking functions for certain use cases. Read More