Data Masking: Masking Social Security and other National IDs
Data masking is one method to combat the nearly 72,000 documented breaches of personally identifiable information (PII) that occur every day. With data privacy breaches still at unacceptably high levels, how can companies protect PII such as their national ID numbers across their myriad sources of data?
IRI’s data masking solutions are delivered in the FieldShield product. FieldShield is a uniquely powerful data-centric security tool that shields fields in ODBC-connected database tables and most (very large) flat file formats. FieldShield allows compliance teams and DBAs to choose a specific data privacy function for each field, based on potential recipients and each field’s need for security, realism, and recoverability.
If the column value needs to be secured now but recovered later, an encryption routine makes sense. If the value is numeric and needs to look real, a FieldShield user could choose a format-preserving encryption algorithm. If the field were a person’s name, a pseudonym function would work better. However, if the data need to be totally secure and not recovered, then masking all, or part of that field with characters like a* or x would be more appropriate.
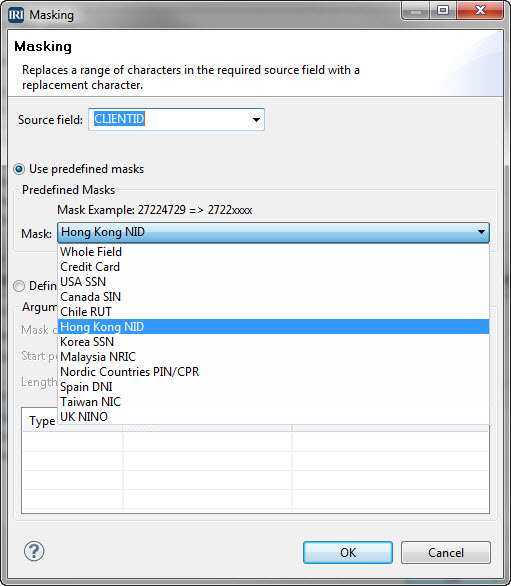
In the United States, it is common to see the ‘x’ data masking character for social security and credit card numbers. The IRI Workbench GUI for FieldShield offers pre-defined masks for multiple national ID numbers, credit card numbers (12 digits), and whole-field redaction where all field digits are replaced.
FieldShield users can also customize their data masking behavior using offset values, offset lengths, and desired data masking characters. Consider the following input sample, where the third field may be a national identification card number:
Robert,07/01/1969,ABC12345
Donald,11/21/1966,DEF34567
Peter,05/31/1955,GHI56789
Mary,12/01/1989,JKL90123
Jill,03/28/2001,MNO45678
That third field, called ID_CODE, could be masked as shown in this FieldShield dialog editor for data masking:
Here is an output sample with data masking applied:
Robert,07/01/1969,^^^12@@@
Donald,11/21/1966,^^^34@@@
Peter,05/31/1955,^^^56@@@
Mary,12/01/1989,^^^90@@@
Jill,03/28/2001,^^^45@@@
While social security and credit card number masking have been the most common requirements that IRI is called to address, FieldShield also supports data masking functions for other national ID numbers in their native formats:
We invite our customers and resellers outside the United States to suggest or request the development of more pre-defined masks that satisfy either national ID formats or specific business needs. Any data privacy masks we create can be added to our library and included in the IRI Workbench for front-end selection.
Leave a comment below, or contact us at fieldshield@iri.com.