
Easier Big Data Prep for R
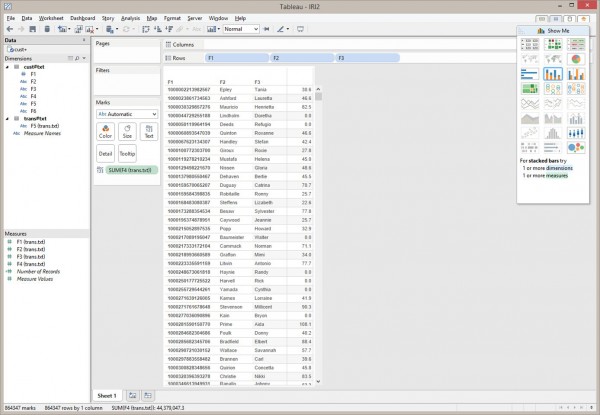
Among analytic tools for statistical computation and graphics, R has shown an increase in popularity among data miners, and in the development of its open source language. Read More

Among analytic tools for statistical computation and graphics, R has shown an increase in popularity among data miners, and in the development of its open source language. Read More
To compete effectively, business users must be able to rapidly produce and present accurate, concise, and compliant information. Whether the analytic discipline is diagnostic, descriptive, predictive, or prescriptive, time-to-visualization matters. Read More
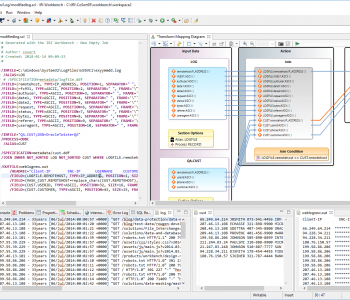
This article is second in a 3-part series on CLF and ELF web log data. We previously explained CLF and ELF web log formats, and now introduce IRI solutions for manipulating and using web log data. Read More

Introduction
The ability to directly move very large database (VLDB) data from/to, and manipulate it within IRI software is essential for those requiring:
big data integration (ETL) database performance optimization (unloads, loads, reorgs, queries) database migration data masking (encryption, redaction, de-identification, etc.) Read More
This is the first of a three-part blog series introducing IRI’s new data structuring technology. This article defines “dark data” and the unstructured sources IRI now supports. Read More

As the old English proverb says, “necessity is the mother of invention.” When it comes to modern business intelligence goals, these words of wisdom ring truer than ever. Read More

Before Big Data became a buzz word and Gartner hype cycle fodder (never mind falling into the ‘Trough of Disillusionment‘), companies like IRI were handling it. Read More

Every land line or cellular telephone call made over a Public Land Mobile Network (PLMN) creates one or more call records. These Call Detail Records (CDRs) or Usage Detail Records (UDRs) are generated by the mobile switching center (MSC) — the primary GSM/CDMA service delivery node responsible for routing voice calls, SMS, and other services. Read More
Data profiling, or data discovery, refers to the process of obtaining information from, and descriptive statistics about, various sources of data. The purpose of data profiling is to get a better understanding of the content of data, as well as its structure, relationships, and current levels of accuracy and integrity. Read More

Note: This article was originally drafted in 2015, but was updated in 2019 to reflect new integration between IRI Voracity and Knime (for Konstanz Information Miner), now the most powerful open source data mining platform available. Read More
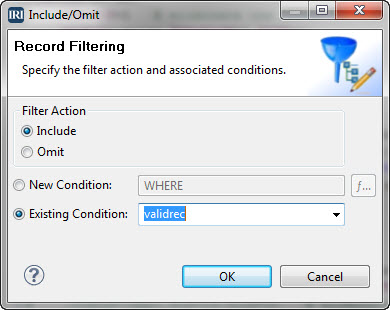
One of the best ways to speed up big data processing operations is to not process so much data in the first place; i.e. to eliminate unnecessary data ahead of time. Read More