
Breached But Still Protected
Data Privacy on Fire For the past 20 years or so, data breach headlines continue to capture public and legal attention. Significant data breaches are chronicled at the Privacy Rights Clearinghouse on this page. Read More

Data Privacy on Fire For the past 20 years or so, data breach headlines continue to capture public and legal attention. Significant data breaches are chronicled at the Privacy Rights Clearinghouse on this page. Read More

Abstract: This article explains a method of protecting credit card data with tokenization using the IRI FieldShield data masking tool.
Submitting one’s credit card details electronically can be disconcerting (e.g., Read More
Data profiling, or data discovery, refers to the process of obtaining information from, and descriptive statistics about, various sources of data. The purpose of data profiling is to get a better understanding of the content of data, as well as its structure, relationships, and current levels of accuracy and integrity. Read More

The increasing sophistication of software applications and the expanding role of database testers require high volumes of high quality, realistic test data that can faithfully represent existing, and stress-test new, platforms. Read More
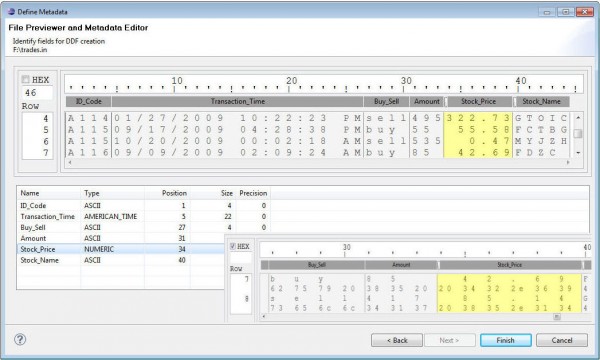
IRI’s data management tools share a familiar and self-documenting metadata language called SortCL. All these tools — including CoSort, FieldShield, NextForm, and RowGen — require data definition file (DDF) layouts with /FIELD specifications for each data source so you can map your data and manage your metadata. Read More
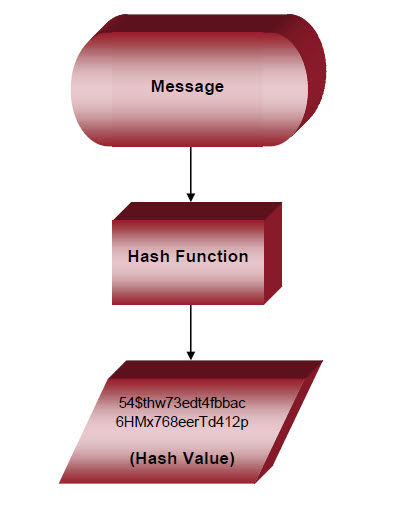
Hashing and encryption are distinct disciplines. Indeed, the differenced between hashing and encryption can be stark:
According to the SSL Store, “encryption is a two-way function where information is scrambled in such a way that it can be unscrambled later. Read More
According to Trent Henry of the Burton Group,
Data protection needs to take into account both internal and external threats, including those against critical database and application resources. Read More
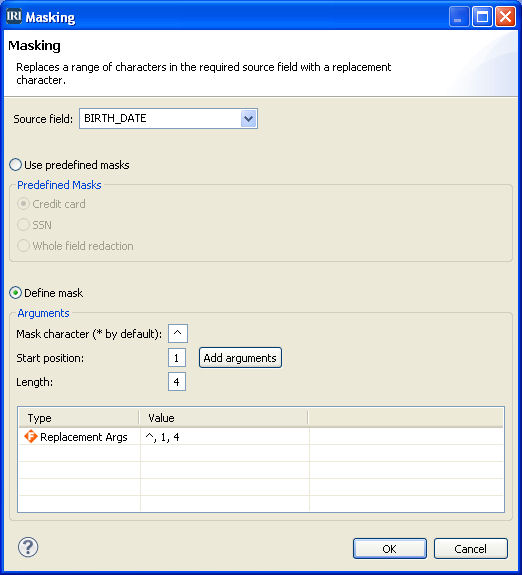
Editors Note: This article covers redacting PII and sensitive information. Specifically, it explains the full or partial column/field redaction of strings in structured databases or flat files. Read More

Summary
The protection of sensitive information and data loss prevention (DLP) are critical elements of modern data governance. IRI’s FieldShield is a uniquely versatile tool for securing sensitive fields in database tables and flat files with a choice of protections that operate according to business rules to de-identify or remove individualizing characteristics, without cutting off access to the rest of the data or changing their basic appearance. Read More

Protecting Data at Rest and in Motion
Database applications that update and query tables may need to secure data going into, or being retrieved from, those tables. Read More

In the course of protecting personally identifiable information (PII) moving into and out of databases, FieldShield and CoSort typically externalize protection of the full table(s) they connect to. Read More