When to Use Hadoop
In the last couple of years since this article about the use of IRI CoSort as a parallel data manipulation alternative to Hadoop, IRI released the Voracity platform to process big data in either paradigm. Read More

In the last couple of years since this article about the use of IRI CoSort as a parallel data manipulation alternative to Hadoop, IRI released the Voracity platform to process big data in either paradigm. Read More
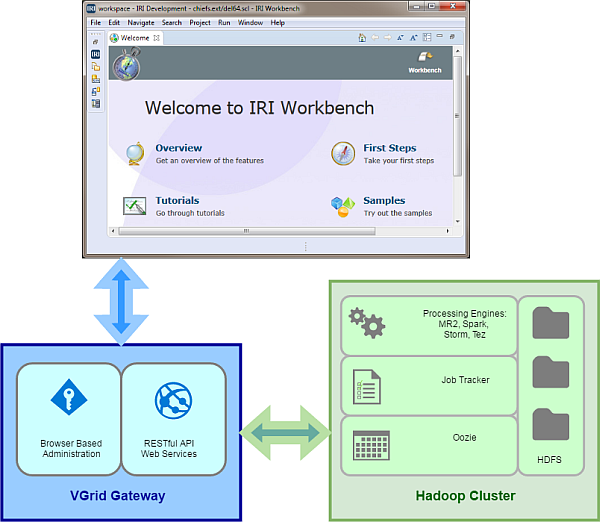
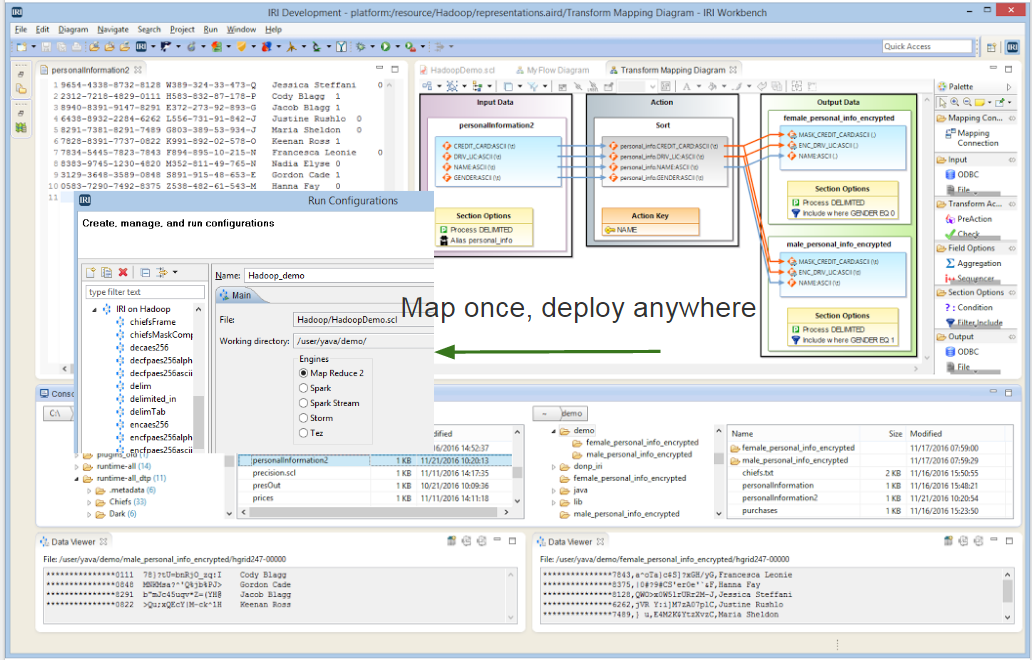
Many of the same data manipulation, masking, and test data generation jobs you can run in IRI Voracity® with the default SortCL program can now also run seamlessly in Hadoop™. Read More
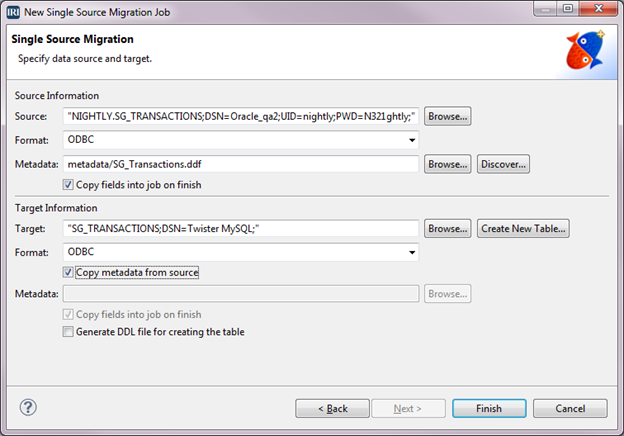
Our first article on data replication in the IRI Workbench GUI for NextForm (DB edition) or Voracity demonstrated how to copy and transform data as it moved from Oracle to two targets. Read More
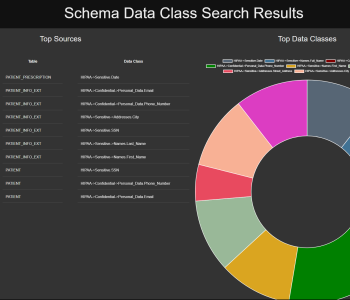
Enterprise data continues to change rapidly in form, size, use, and residence. Rarely does it remain in siloed constructs anymore, limited to certain business units or untouched by the outside world. Read More
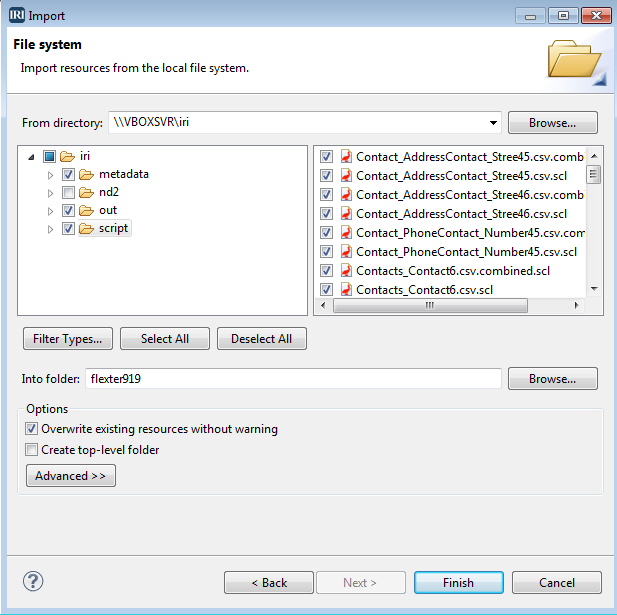
Sonra recently demonstrated the processing of complex XML data in the IRI Voracity data management platform with the help of Sonra’s Flexter Data Liberator software. Flexter and Voracity are a match made in heaven. Read More
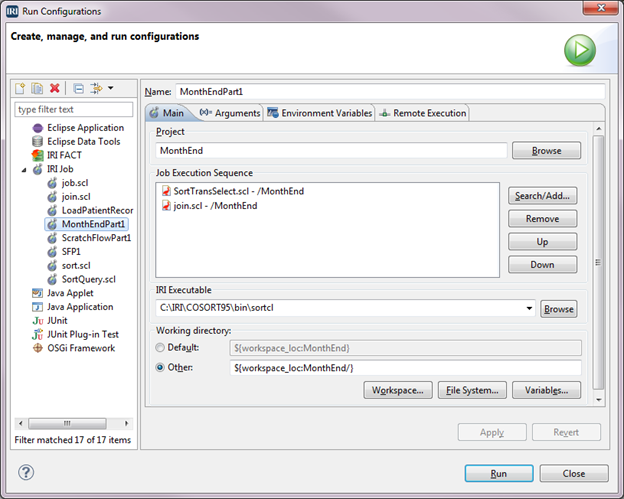
IRI Workbench not only has several ways to create jobs, but also several ways to execute them.
This article focuses on IRI Workbench execution options for job scripts based on the SortCL program language, which covers IRI Voracity ETL, CDC, SDC, pivoting and subsetting jobs, as well as its constituent product functions; i.e., Read More
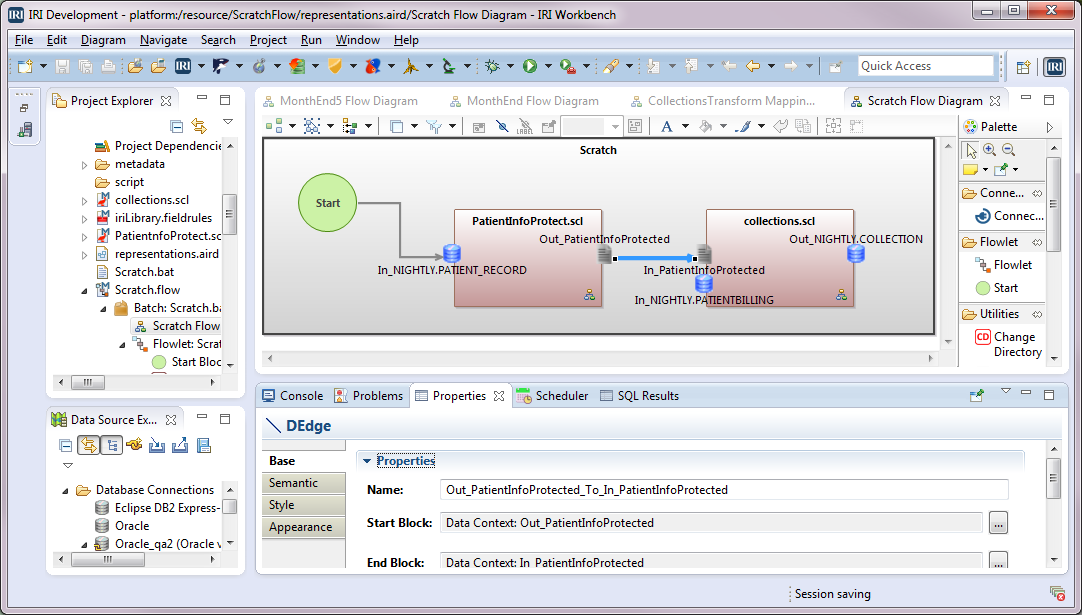
This is the second of two articles on creating a new IRI Voracity® ETL job flow from the job design Palette in the IRI Workbench, built on Eclipse. Read More
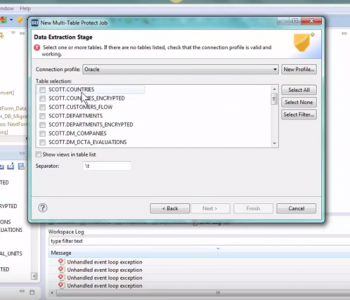
In this demonstration, the Multi-Table Protect Job Wizard in the IRI Workbench GUI for Fieldshield and Voracity is used to define a rule for data in multiple Oracle tables. Read More
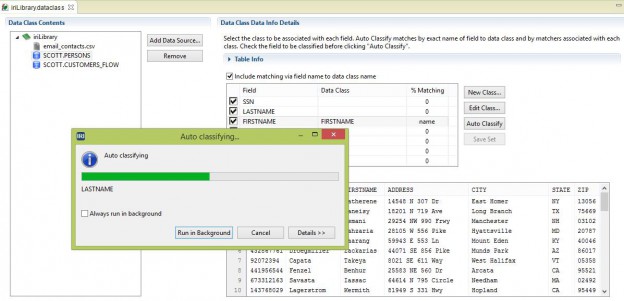
EDITOR’S NOTE: The information documented in this article applies to IRI Workbench versions released prior to Q4, 2023. For more recent information, please refer instead to this article. Read More
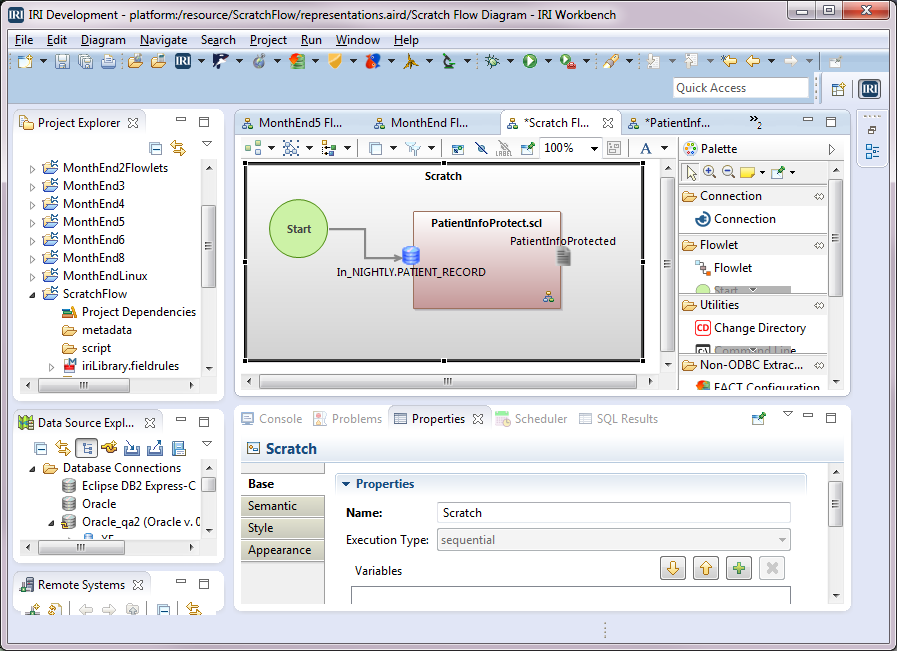
This is the first of two articles showing how to create and use job flows in the IRI Workbench GUI for Voracity. It follows two other series on creating flows automatically using new job wizards. Read More
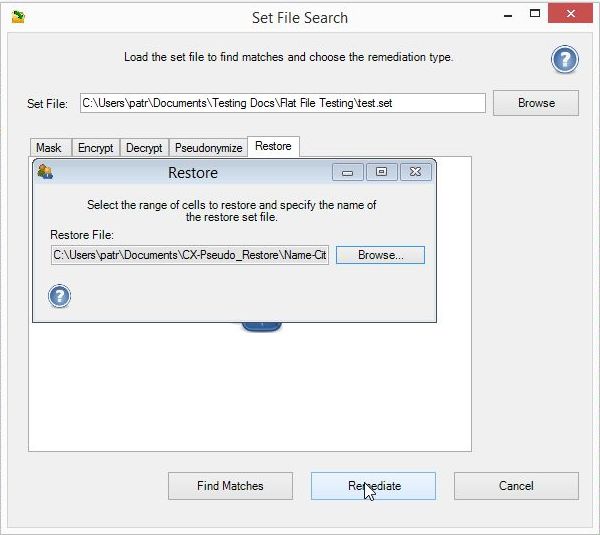
Editor’s Note: This article was writen in 2016. But since 2023, there are even more robust PII discovery capabilities for data in structured, semi-structured, and unstructured (RDB, NoSQL DB, file, document, and image) sources using IRI DarkShield, including Named Entity Recognition (NER) model matchers. Read More