Data Masking/Protection
Data Masking/Protection
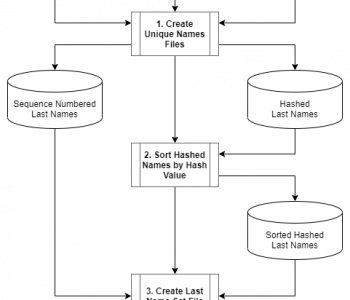
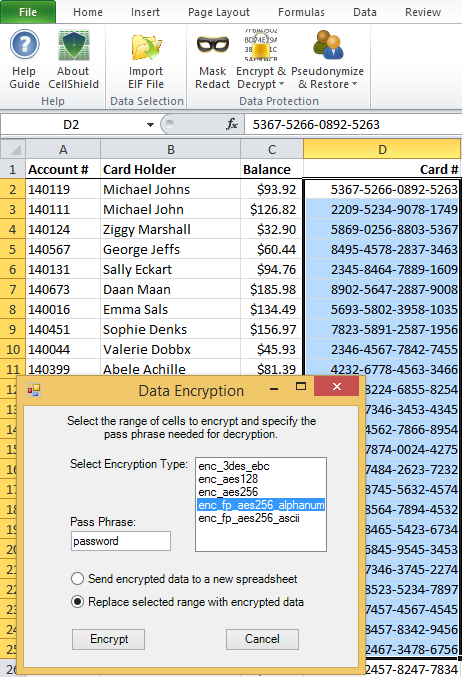
Pseudonym Hash Set (File) Creation Wizard
In conjunction with a newly created wizard used to generate Pseudonym Hash Replacement Rules, based on the same concept discussed in a previous article, a Pseudonym Hash Set File Creation Wizard is now also available in IRI Workbench. Read More