
Masking Data for CMMC Compliance
Abstract
The Cybersecurity Maturity Model Certification (CMMC) is a cornerstone of the U.S. Department of Defense (DoD) strategy to safeguard Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) across the Defense Industrial Base (DIB). While CMMC defines what safeguards must be implemented, defense contractors and their consultants still need practical, auditable technologies to operationalize those requirements consistently and at scale.
This article maps CMMC 2.0 requirements—particularly those aligned with NIST SP 800-171 and SP 800-172—to IRI’s data discovery and masking software, including DarkShield® and the IRI Data Protector Suite®. It demonstrates how a data-centric security approach helps primes and subcontractors alike reduce compliance scope, enforce least privilege, and produce defensible assessment evidence.
Understanding CMMC in a Data-Centric Context
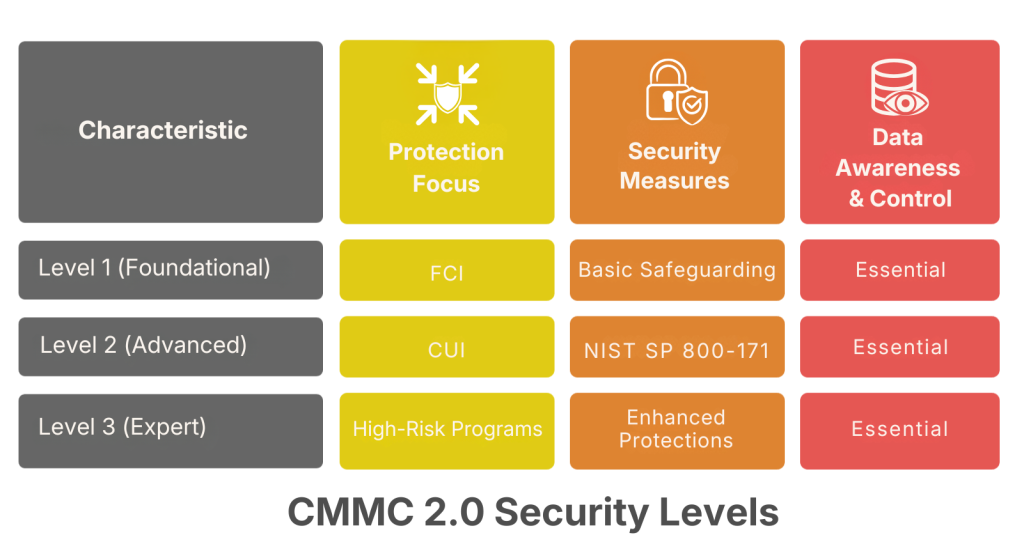
CMMC 2.0 consolidates security expectations into three levels:
- Level 1 (Foundational): Protection of FCI using basic safeguarding practices.
- Level 2 (Advanced): Protection of CUI aligned with NIST SP 800-171.
- Level 3 (Expert): Enhanced protections for high-risk programs (based on select NIST SP 800-172 controls).
Across these levels, a recurring theme is data awareness and control: knowing where sensitive data exists, who can access it, and how it is protected throughout its lifecycle. This is where automated data discovery and masking become essential.
Why Data Discovery and Masking Matter for CMMC
Many CMMC controls implicitly assume that organizations can accurately:
- Identify FCI and CUI across structured, semi-structured, and unstructured sources
- Minimize exposure of sensitive data in non-production, analytics, and test environments
- Enforce least privilege by reducing the presence of clear-text sensitive data
- Demonstrate repeatable, auditable protection mechanisms
Manual processes and point tools struggle to meet these expectations at scale—especially in hybrid, multi-cloud, and legacy environments common in the DIB.
Overview of IRI Data Discovery and Masking Capabilities
IRI provides an integrated, data-centric approach to sensitive data protection:
- IRI DarkShield®: Automated discovery, classification, and masking of sensitive data—including CUI, PII, PHI, PCI, and IP—across files, documents, images, databases, and big data platforms.
- IRI FieldShield® / CellShield®: High-performance, rule-based masking for structured data at rest and in motion.
- IRI Voracity®: A unified data management platform that combines discovery, ETL, data quality, and masking for governed analytics and AI readiness.
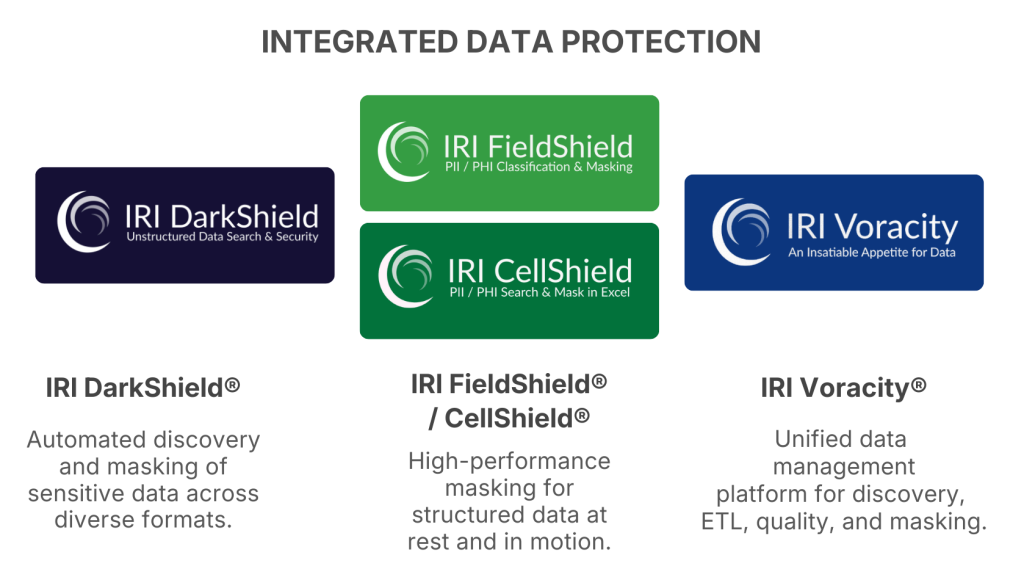
Together, these tools support continuous discovery, policy-driven masking, and provable enforcement aligned with CMMC objectives.
Mapping CMMC Practices to IRI Capabilities
The table below summarizes how key CMMC practice areas align with specific IRI capabilities. Detailed explanations follow.
| CMMC Practice Area | Representative CMMC / NIST Controls | IRI Capability | Compliance Outcome |
| Asset & Data Identification | CMF.L2-3, NIST 3.4.1 | Centralized data discovery and classification | Accurate FCI/CUI scoping |
| Access Control / Least Privilege | AC.L2-3, NIST 3.1.x | Policy-driven masking and role-based exposure | Reduced unauthorized access |
| Data Protection | MP, SC, IA families | Data masking, encryption, redaction, etc. | Prevention of clear-text exposure |
| Media & Non-Prod Sanitization | MP.L2, NIST 3.8.x | Static and real-time test data masking | Safe Dev/Test and data sharing |
| Risk Management | RMF-aligned practices | Discovery reports and risk metrics | Reduced breach impact |
| Audit & Accountability | AU.L2-3, NIST 3.3.x | Repeatable jobs, logs, reports | Verifiable assessment evidence |
1. Asset Identification and Data Location (CMMC Level 1–3)

CMMC Focus: Understanding where FCI and CUI reside.
IRI Alignment:
- DarkShield scans file systems, object stores, databases, and document repositories to locate sensitive data using pattern matching, dictionaries, NLP, and context rules.
- Supports structured and unstructured data, including PDFs, Office documents, images, and logs.
Compliance Value: Enables accurate CUI scoping, a prerequisite for Level 2 certification.
2. Access Control and Least Privilege (Level 2–3)
CMMC Focus: Limiting access to sensitive information.
IRI Alignment:
- Irreversible masking, pseudonymization, fabrication, and other deterministic or non-deterministic masking functions reduce the presence of live CUI in lower-trust environments.
- Role-based masking rules ensure users and systems only see what they are authorized to see.
Compliance Value: Reduces insider threat and audit findings related to overexposed data.
3. Data Protection and Media Sanitization (Level 2–3)

CMMC Focus: Preventing unauthorized disclosure of CUI.
IRI Alignment:
- Persistent or dynamic masking protects data at rest, in motion, and in use.
- Supports test data management (TDM) use cases where production CUI must not propagate.
Compliance Value: Demonstrates proactive control rather than reactive remediation.
4. Risk Management and Incident Impact Reduction (Level 2–3)
CMMC Focus: Limiting the impact of a breach.
IRI Alignment:
- Masked or redacted data has no operational value to attackers.
- Discovery reports help quantify residual risk and prioritize remediation.
Compliance Value: Supports risk-based decision-making required by NIST-aligned controls.
5. Auditability and Continuous Monitoring (Level 2–3)

CMMC Focus: Evidence-based compliance.
IRI Alignment:
- Detailed logs, reports, and repeatable jobs show when, where, and how data was discovered and protected.
- Policies can be re-run to support continuous compliance rather than one-time assessments.
Compliance Value: Simplifies preparation for CMMC assessments and POA&M tracking.
Common Deployment Patterns in the Defense Ecosystem
Both prime contractors and subcontractors commonly deploy IRI data discovery and masking in the following scenarios:
- Pre-assessment CUI discovery to establish and document CMMC certification scope
- Data minimization for Dev/Test and training environments supporting engineering and sustainment programs
- Redaction and masking of shared documents exchanged with primes, subs, and government stakeholders
- Analytics and AI enablement using masked, yet analytically valid, data to support logistics, readiness, and program insights.
- Subcontractor flow-down compliance where primes require demonstrable CUI protections across the supply chain
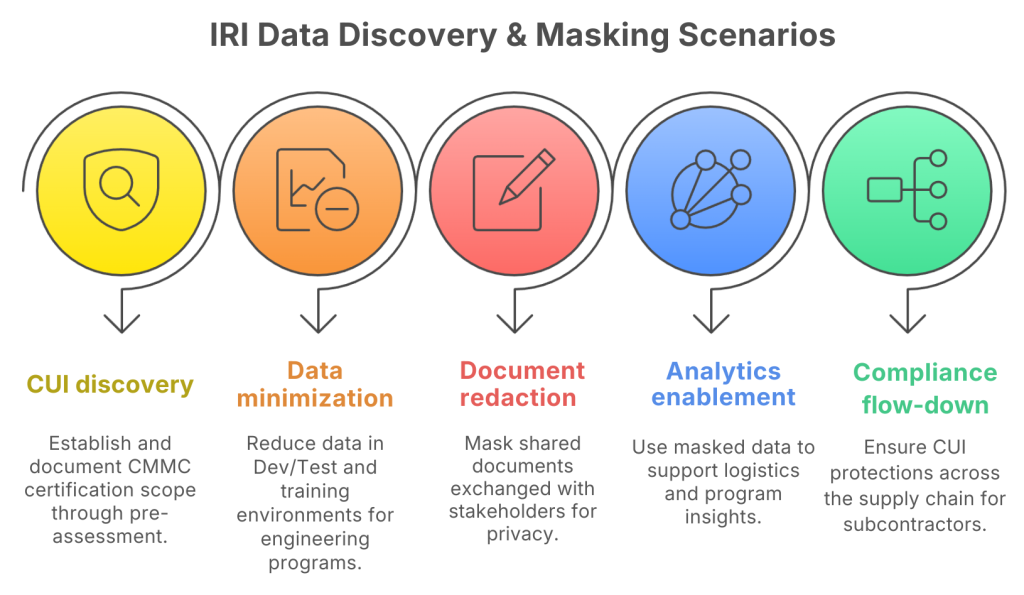
These patterns support compliance while preserving operational efficiency.
- Pre-assessment CUI discovery to establish certification scope
- Data minimization for Dev/Test environments
- Redaction of shared documents sent to primes, subs, or government stakeholders
- Analytics and AI enablement using masked but analytically valid data
FAQs: CMMC and IRI Data Protection
Q: Does CMMC explicitly require data masking?
No, but many NIST SP 800-171 practices are challenging to meet without it.
Q: Is data discovery required for CMMC Level 2?
It is not named explicitly, but accurate CUI identification is mandatory.
Q: Can IRI tools help define CUI scope?
Yes. DarkShield is commonly used to locate and classify CUI before assessments.
Q: Does masking replace encryption?
No. Masking complements encryption by reducing exposure in authorized use cases.
Q: Can IRI handle unstructured CUI like PDFs and emails?
Yes, including scanned documents and images.
Q: Is masked data still usable for testing and analytics?
Yes. IRI supports format-preserving and rule-based masking.
Q: Does this help with insider threat mitigation?
Yes, by eliminating unnecessary access to clear-text data.
Q: How does this support least privilege?
By ensuring sensitive values are never present where they are not required.
Q: Can discovery rules be customized to agency definitions of CUI?
Yes, using extensible pattern libraries and policies.
Q: Is this applicable to cloud and hybrid environments?
Yes, including on-prem, cloud, and big data platforms.
Q: Does IRI provide reporting for auditors?
Yes, with detailed discovery and masking reports.
Q: Can IRI tools run continuously?
Yes, supporting ongoing compliance monitoring.
Q: Does masking impact application performance?
IRI masking is designed for high performance and scalability.
Q: Is this relevant to Level 1 contractors?
Yes, especially for FCI minimization and future readiness.
Q: How does this help beyond compliance?
It improves security posture, reduces breach impact, and enables safer data reuse.
Conclusion
CMMC compliance is ultimately about reducing risk to sensitive defense information. IRI’s data discovery and masking software provides the technical means to operationalize CMMC requirements with precision, scalability, and auditability. For defense contractors and consultants, a data-centric approach not only accelerates certification but also builds a stronger, more resilient security foundation for the long term.











