The 1996 Health Insurance Portability and Accountability Act (HIPAA) is now being regularly enforced across the country, and fallout from breaches of protected health information (PHI data) remains constant, and damaging. If you're a "covered entity" under HIPAA, what are you and your business associates doing about HIPAA compliance as it relates to PHI protection?
The pages in this section of the IRI web site take a closer look at the key US healthcare data security rules and how you can comply with them (and prove it). If you would like more information or need help, contact us to learn how we have helped others, and can help you.
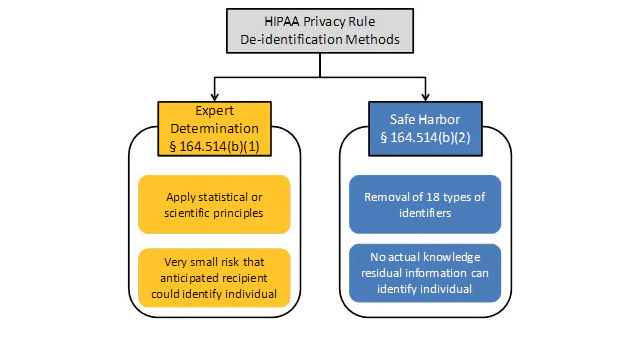
PHI subject to the HIPAA Safe Harbor security rule, regulations like 45 CFR 164.312 and 170.210 specify encryption or hashing of 18 key (direct, unique) identifiers. Long-proven data masking tools from IRI support HIPAA security rule compliance with multiple data obfuscation and data anonymization functions within job wizards purpose-built for the discovery and consistent de-identification of protected health information.
More specifically, the built-in data classification and masking functions in the IRI FieldShield, DarkShield, and CellShield data masking tools -- or the IRI Voracity platform which includes them -- help you find, catalog, and de-identify PHI in structured, semi-structured, and unstructured data sources automatically.
These sources (whether in your on-premise network or cloud infrastructure) include: relational and NoSQL databases; flat and free-text files; Excel, PDF and Word documents; PowerPoint presentations; HL7, X12 and FHIR EDI files; DICOM studies; Parquet and audio files; and, most popular image file formats.

Alternatively, the HIPAA Expert Determination Method Rule, allows compliance through certified mitigation of re-identification risk. Integrated re-ID risk scoring and anonymization technology in IRI data masking software statistically measures that risk, and blurs quasi-identifiers to comply with this rule, too.
De-Identification
De-identification refers to processes that disassociate personally identifiable information (PII) within protected health information (PHI) repositories and other "data at risk."
PHI de-identification is a specific requirement in the healthcare industry, where for example, it is used in both "safe harbor" and "expert determination method" practices in medical research (to remove patient identities from study models). De-identification is also a blanket term referring to the anonymization or masking of PII in many other industries.
The most recent Security Rule in HIPAA regulations (45 CFR Parts 160 and 164) spell out the compliance requirements for those entities managing PHI. HIPAA rules apply to 18 specific identifiers:
|
Name |
Address |
Birthdate |
|
Phone # |
Fax # |
Email Address |
|
Social Security # |
Medical Record # |
Health Insurance Beneficiary # |
|
Account # |
Certificate # |
Vehicle ID # |
|
Device ID # |
Personal URL |
IP Address |
|
Biometric ID |
Facial Image |
Other Unique ID Code |
Each of the data masking software products in the IRI Data Protector suite helps you find and classify, and then protect PII, PAN, PHI, etc. in multiple data sources for Safe Harbor rule compliance. They also work hand-in-hand with included re-ID risk scoring technology for compliance with the Expert Determination Method rule. See this article in HIPAA Journal for more information about what constitutes PHI.
HIPAA compliance requires either:
Redaction - Safe Harbor
Manipulating, masking, or removing these key identifiers so that it is difficult or impossible to identify an individual or restore the original data.
De-Identification - Expert Determination Method
Stripping the identifiers, and generalizing quasi-identifiers until an expert determines the statistical risk of re-identification is very low.
In addition to healthcare data protection software, IRI can also deliver professional services and refer you to expert statisticians, HIPAA consultancies, and regulatory attorneys with whom we partner.
You can leverage these tools and teams as needed to obtain compliance certification and cybersecurity insurance, and to defend against fines or breach-related claims. See our free course details below:

HIPAA Data Compliance Course
A three-hour HIPAA Compliance online course covering PHI de-identification and masking on structured, semi-structured, and unstructured sources of data on-premise and in the cloud, plus and re-ID risk scoring processes on structured data. It also includes information related to compliance certification, breach insurance, and breach claim defense.
Blog Article
Other Resources


