Challenges
More data privacy laws -- like those tabbed across this section -- in the US, Europe, and other international jurisdictions are passing and being enforced. CISOs and data governance teams responsible for safeguarding data at risk must also prove they located and protected that data in the right places, and in the right ways.
Data Loss Prevention (DLP) systems and data masking software can discover and de-identify Personally Identifiable Information (PII). How well do these data masking tools document their search results, and actual masking procedures?
In addition, how easy is it to locate and modify specific protections if something needs to be redone, or done differently? How can the risk of re-identification based on quasi-identifying data be measured and mitigated? And even the best data masking tools for compliance with one data privacy law may not be the best way to address another law.
Solutions
For detection control and data breach prevention, extensive search logs and dashboard reports are available for compliance officer inspection. They are accessed from the data profiling and sensitive data discovery modules included with all IRI data masking software.
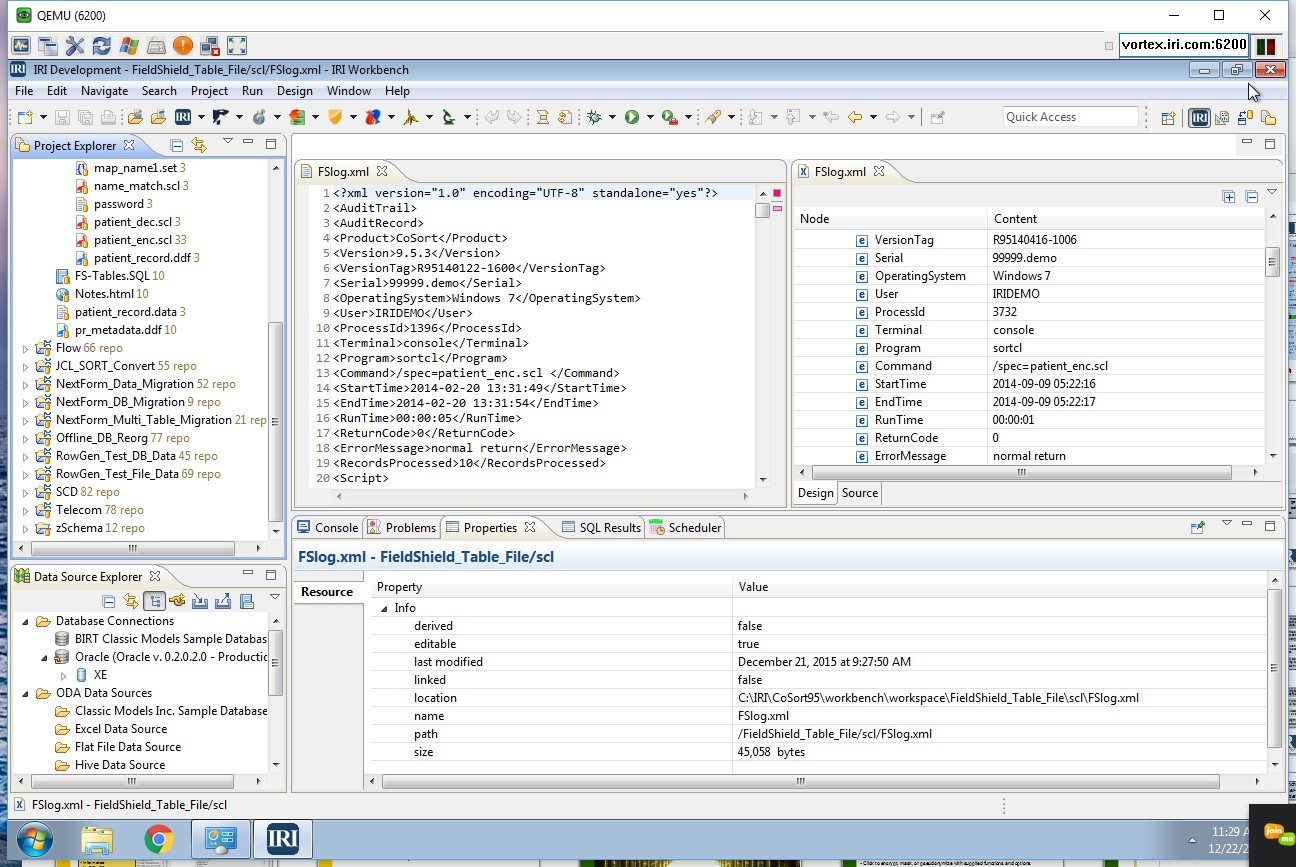
For example, there are both scan-specific text reports and visualizations like these for structured data:
.png)
For data masking operations, all the source and target details -- and the masking functions applied -- are specified in self-documenting, human-readable job scripts, mapping diagrams, or configuration files, plus audit logs produced by: IRI FieldShield, IRI DarkShield and IRI CellShield EE (which are all also included in the IRI Voracity data management platform).
In the case of FieldShield, the audit trail contains each job script, which shows the protection technique(s) applied to each field in each table or file processed. Source-to-target mapping diagrams show the same changes quickly with orange connecting lines (see the screenshot below) and the visual representations of the jobs are handy images to share.
That XML audit log also contains other job metadata for compliance verification, like the:
- protection library function(s) used
- encryption keys or de-ID codes
- input and output tables or files
- user who ran the job
- job start and end times
- number of records processed
For example, masking the SSN field in a payroll feed is a matter of connecting to your sources (or existing jobs) and clicking through a new job wizard or modifying existing parameters in a dialog or script. Some of the data masking functions you can apply (ad hoc or as a rule), are:
- encryption and decryption
- anonymization via pseudonymization
- data blurring, hashing, deletion or scrambling
- de-identification and re-identification
- partial or full-field redaction
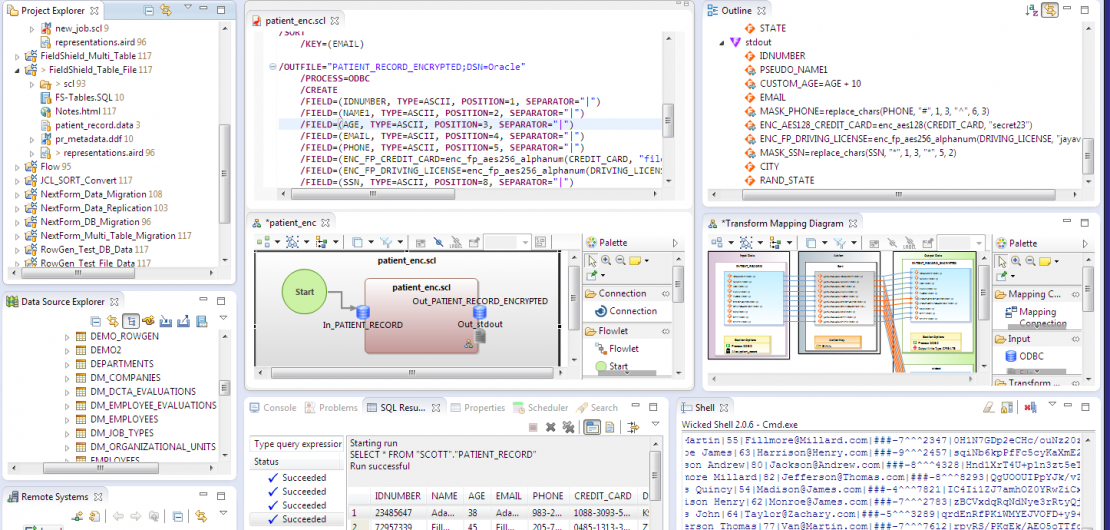
As a compliance officer, you can see the protection(s) in each exportable self-documenting job script or diagram. Once approved, the job can be saved or run on any local or remote server running the IRI data masking executable.
After execution, the job script can be isolated or shared, and modified or protected using EGit for example, for reliable re-use in production. In FieldShield, a re-ID risk scoring module is also supplied to statistically measure the likelihood of a data set being linked to an individual based on the unmasked quasi-identifying (demographic) attributes in their record. Further data anonymization techniques like blurring and bucketing to lower re-ID risk but preserve data utility for research and marketing purposes are included (see the HIPAA and FERPAtabs above).
In the case of IRI DarkShield, another comprehensive set of dashboard charts are produced to show data discovered (and if applicable, masked) in structured, semi-structured, and unstructured sources. One of those charts is a bubble chart to help you rank the risk of each data source; a kind of instant vulnerability assessment (heat map) resulting from aggregated data discovery (search) jobs:
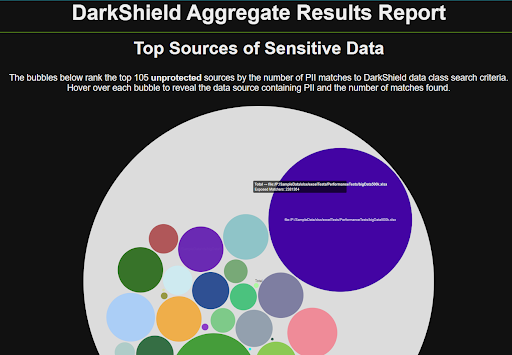
This data can also be audited in machine-readable searching and masking artifacts in IRI Workbench, or exported to SIEM tools like Splunk Enterprise Security for further analysis and action.
In the case of IRI CellShield EE, both data discovery results and masking operation audit trails are provided in Excel, and linked for export to email, Splunk and Datadog.
The logs described on these page can show you how to protect PII and sensitive data, but are only part of the data privacy compliance solutions from IRI. To learn more about these logs and forensics in GDPR and HIPP data masking generally, see this page. Also, check out the data lineage options on this page.
Related Solutions
Related Products


