Challenges
Every encrypted data item can only be decrypted with an encryption key. Managing key access and storage is, therefore, important; but it can also be challenging.
Mislaid keys can mean valuable data loss. Thousands of items may be protected by different algorithms and keys. Stolen keys can result in data breach and misuse.
Solutions
The IRI FieldShield and IRI DarkShield data masking tools in the IRI Data Protector suite and IRI Voracity platform provide several ways to manage encryption keys. One way is to specify the keys directly within each field encryption or decryption specification.
This is consistent with this Gary Palgon's advice:
"Centralize key management with distributed execution. A solution that employs a hub-and-spoke architecture for distributed key management allows encryption and decryption nodes to exist at any point within the enterprise network. Spoke key-management components are easily deployed to those nodes and integrated with the local encryption applications. Once the spoke components are active, all encryption and decryption of the formerly clear text data is performed locally to minimize the risk of a network or single component failure having a large impact on overall data security."
- Enterprise System Journal
Other ways include: specifying them in a hidden and/or secure key file, through an environment variable, or by using a public/private key pair system.
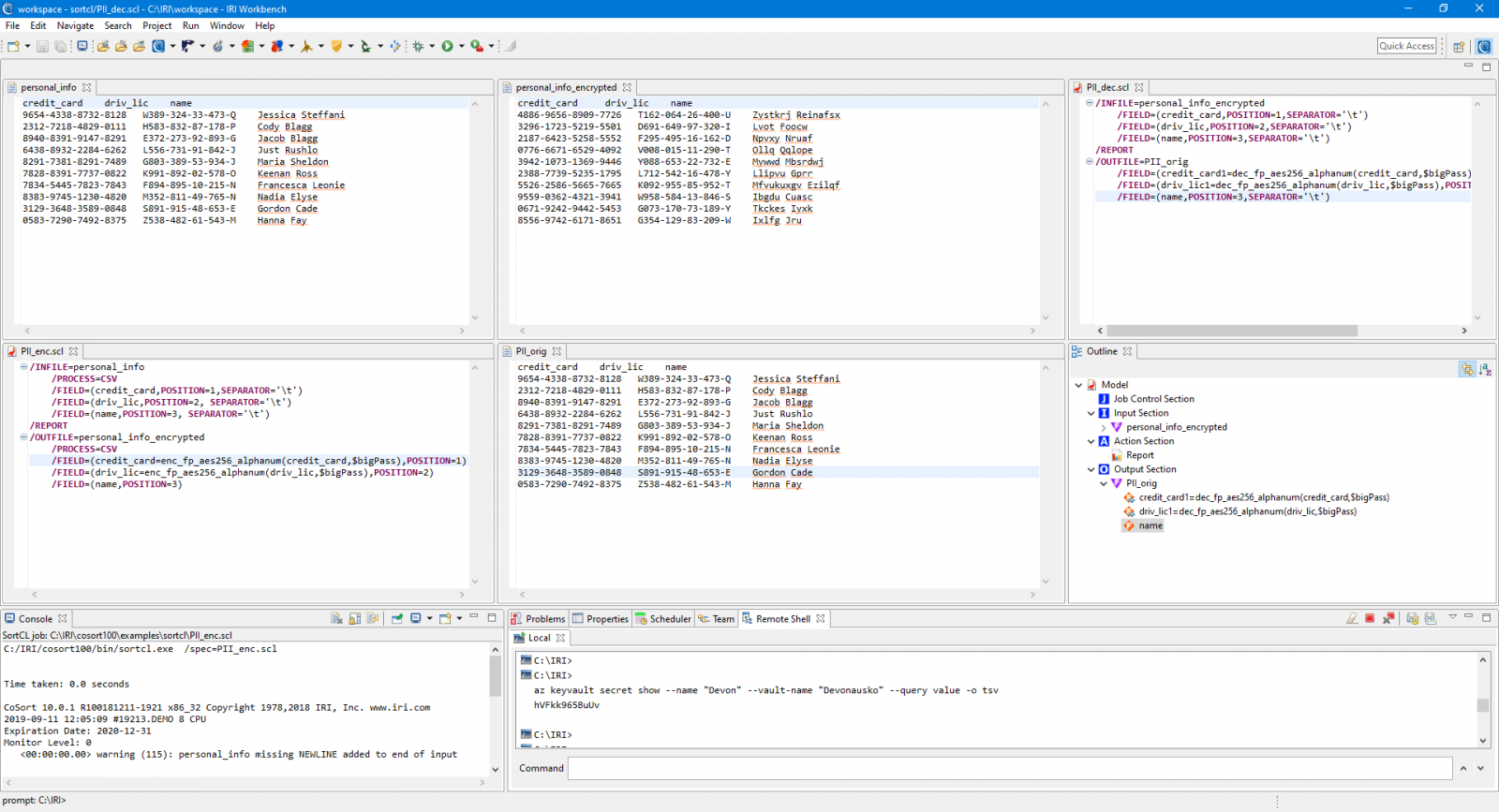
You can also work with IRI to integrate your key provisioning or storage appliance to these methods. The example below shows the use of FieldShield with encryption keys stored in the Azure Key Vault. You can also manage these keys in Alliance Key Manager from Townsend Security to leverage its HSM and other advanced features.
See also
Blog > Data Masking > Encryption Key Management
Blog > Data Masking > Securing FieldShield Passphrases in Azure Key Vault
Blog > Data Masking > Securing FieldShield Encryption Keys with Alliance Key Manager


