Frequently Asked Questions (FAQs)
1. What is tokenization in data masking?
Tokenization is a method of replacing sensitive data, such as a credit card number, with a non-sensitive equivalent called a token. This token has no exploitable meaning or value outside of its mapped environment and is often used to meet PCI DSS compliance requirements.
2. How does tokenization differ from encryption?
Encryption protects data by encoding it, and the data is still recoverable with the correct decryption key. Tokenization, on the other hand, replaces the data entirely with a random token that has no mathematical relationship to the original data, making it useless if breached.
3. What are the advantages of using tokenization for PCI compliance?
Tokenization significantly reduces the risk of exposing sensitive payment card data. Since the original data is replaced with a meaningless token, systems storing only tokens may be exempt from PCI DSS scope, lowering audit and compliance burdens.
4. Can tokenization be used with encryption together?
Yes. IRI allows tokenization to be used in combination with format-preserving encryption (FPE). This provides layered protection where encrypted data can first be tokenized to add an extra layer of abstraction and access control.
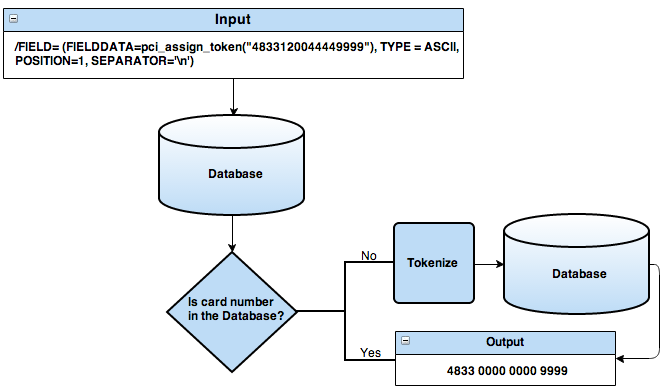
5. How does IRI’s tokenization function work?
IRI’s tokenization function in FieldShield or Voracity jobs maps original values like credit card numbers to an existing or generated token. This token can then be stored, transmitted, or processed without revealing the original data unless detokenized by an authorized user.
6. What types of data can be tokenized using IRI FieldShield?
While primarily used for PANs (Primary Account Numbers) to meet PCI DSS requirements, IRI FieldShield can also tokenize other structured sensitive data such as social security numbers, customer IDs, or phone numbers.
7. Can tokens be reversed to retrieve the original data?
Yes, IRI’s tokenization process can be designed to support detokenization for authorized users. This makes it possible to retrieve the original value when necessary, such as during payment processing or customer service activities.
8. What makes tokenization secure against data breaches?
Tokens have no intrinsic value and cannot be used to derive the original data. Even if intercepted, they provide no exploitable information, especially when securely stored and mapped in a controlled token vault or algorithm.
9. How can IRI help implement tokenization securely?
IRI offers Professional Services to help organizations implement PCI-compliant tokenization logic. This includes securing the tokenization function, customizing logic if needed, and integrating it with other masking or encryption methods.
10. Can I use tokenization in unstructured data environments?
Tokenization in IRI is primarily applied to structured data in fields. For unstructured data environments, other IRI tools like DarkShield may be used to locate and mask sensitive values, though pure tokenization is best suited to defined, structured elements.