Challenges
The purpose of most encryption tools and techniques is to mask data and allow it to be decrypted. Unfortunately, their processes result in ciphertext that is not human readable and is often longer than the original field value.
The challenge is to retain the original format of the data in its protected state, so that it appears real, preserves referential integrity checks, and can be used for testing.
Data protection needs to take into account both internal and external threats, including those against critical database and application resources. However, many protection mechanisms require application retooling or add complexity that delays or halts deployment. Format-preserving encryption overcomes these issues. It's an exciting step toward improved, simpler data protection and compliance with regulatory requirements.
-Trent Henry, Burton Group
Solutions
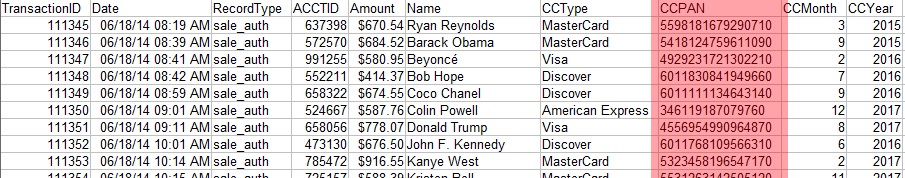
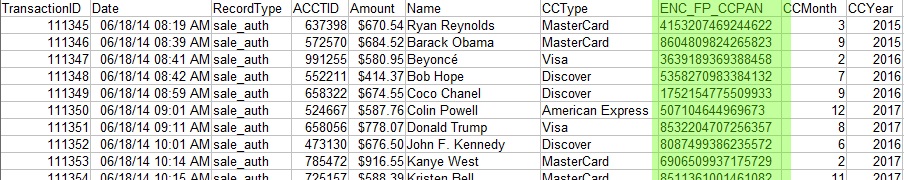
IRI's data masking softawre products encrypt personally identifiable information (PII) in databases and files with advanced (AES-128 and AES-256) Format-Preserving Encryption (FPE) technology. Harden your data one column (or field) at a time without altering the format or appearance of the original values.
With IRI FieldShield (for databases and flat files), IRI CellShield (for Excel), IRI DarkShield (for unstructured files), or IRI Voracity (for DBs, files, HDFS, etc.), you can apply ad hoc or global FPE functions on a rule-basis to:
- Keep and preserve original data formats
- Maintain referential integrity
- Eliminate the need for multiple masking and lookup tables
- Eliminate format changes, database, or application schema
- Encrypt primary and foreign keys
- Provide reversible data masking
For example, encrypt a 16-digit credit card number and display another 16-digit number in the same format: